UK and South Korea: Hackers use zero-day in supply-chain attack

The National Cyber Security Centre (NCSC) and Korea’s National Intelligence Service (NIS) warn that the North Korean Lazarus hacking group breaches companies using a zero-day vulnerability in the MagicLine4NX software to conduct supply-chain attacks.
MagicLine4NX is a security authentication software developed by the South Korean company Dream Security, used for secure logins in organizations.
According to the joint cybersecurity advisory, the DPRK-based threat actors leveraged a zero-day vulnerability in the product to breach their targets, primarily South Korean institutions.
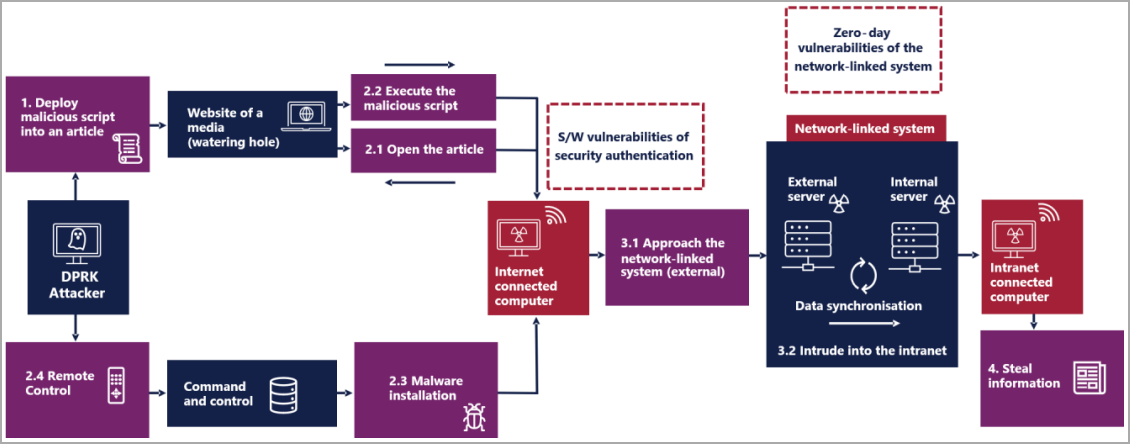
“In March 2023, cyber actors used the software vulnerabilities of security authentication and network-linked systems in series to gain unauthorized access to the intranet of a target organization,” describes the advisory.
“It used a software vulnerability of the MagicLine4NX security authentication program for the initial intrusion into an internet-connected computer of the target and exploited a zero-day vulnerability of the network-linked system to move laterally and gain unauthorized access to information.”
The attack started with compromising a media outlet’s website to embed malicious scripts into an article, allowing for a ‘watering hole’ attack.
When specific targets from certain IP ranges visited the article on the compromised site, the scripts executed malicious code to trigger the mentioned vulnerability in the MagicLine4NX software, impacting versions prior to 1.0.0.26.
This resulted in the victim’s computer connecting to the attackers’ C2 (command and control) server, allowing them to access an internet-side server by exploiting a vulnerability in a network-linked system.
Using the data synchronization function of this system, the North Korean hackers spread information-stealing code to the business-side server, compromising PCs within the target organization.
The dropped code connected to two C2 servers, one acting as a gateway in the middle and the second located externally on the internet.
The function of the malicious code includes reconnaissance, data exfiltration, downloading and executing encrypted payloads from the C2, and lateral network movement.
Detailed information about this attack, codenamed ‘Dream Magic’ and attributed to Lazarus, can be found in this AhnLab report, available only in Korean.
Lazarus supply chains
State-backed North Korean hacking operations consistently rely on supply chain attacks and the exploitation of zero-day vulnerabilities as part of their cyber warfare tactics.
In March 2023, it was discovered that “Labyrinth Chollima,” a subgroup of Lazarus, conducted a supply chain attack against VoIP software maker 3CX to breach multiple high-profile companies worldwide.
Last Friday, Microsoft disclosed a supply chain attack on CyberLink that the Lazarus hacking group used to distribute trojanized, digitally-signed CyberLink installers to infect at least a hundred computers with the ‘LambLoad’ malware.
The North Korean hacking group uses these types of attacks to target specific companies, whether for cyber espionage, financial fraud, or cryptocurrency theft.
Earlier this year, the Cybersecurity Advisory (CSA) warned that the funds stolen in attacks by the North Korean hackers are used to fund the country’s operations.
“The authoring agencies assess that an unspecified amount of revenue from these cryptocurrency operations supports DPRK national-level priorities and objectives, including cyber operations targeting the United States and South Korea governments—specific targets include Department of Defense Information Networks and Defense Industrial Base member networks,” reads an advisory from CISA.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


