Update now! Chrome needs patching against two in-the-wild exploits
A day late and a dollar short is a well-known expression that comes in a few variations. But this version has a movie and a book to its name, so I’m going with this one. Why?
Google has published an update for the Chrome browser that patches two newly discovered vulnerabilities. The browser’s Stable channel has been updated to 89.0.4389.128 for Windows, Mac and Linux. Both being exploited in the wild.
Google is aware of reports that exploits for CVE-2021-21206 and CVE-2021-21220 exist in the wild.
Note that other browsers, such as Edge, Brave and Vivaldi are also based on Chrome and likely to be affected by the same issues.
Which vulnerabilities are patched?
Publicly disclosed computer security flaws are listed in the Common Vulnerabilities and Exposures (CVE) database. Its goal is to make it easier to share data across separate vulnerability capabilities (tools, databases, and services).
The first zero-day was listed as CVE-2021-21220 and was discovered at the Pwn2Own 2021 event last week. The vulnerability is caused by insufficient validation of untrusted input in V8, Google’s high-performance JavaScript and WebAssembly engine that interprets code embedded in web pages.
The second zero-day was listed as CVE-2021-21206 and is described as a “use after free in Blink”. Use after free (UAF) is a vulnerability caused by incorrect use of dynamic memory during a program’s operation. If after freeing a memory location, a program does not clear the pointer to that memory, an attacker can use the error to manipulate the program. Blink is the name of the rendering engine used by Chromium to “draw” web pages.
Why did I say a day late?
Researcher Rajvardhan Agarwal managed to publish a working exploit for CVE-2021-21220 (the vulnerability discovered at Pwn2Own) on GitHub over the weekend, by reverse-engineering a patch produced by the Chromium team. Chromium is the open source browser that Chrome is built upon, and it in turn is made up of components, like V8 and Blink. Fixes appear in Chromium first, and then Google packages them up, along with some Google-specific goodies, into a new version of the Chrome browser.
And why a dollar short?
Because the same researcher stated that (at the time) although the vulnerability affecting Chromium-based browsers had been patched in the latest version of V8, it worked against the current Chrome release, thereby leaving users potentially vulnerable to attacks.
Luckily, although Agarwal proved that exploitation was possible, he stopped short of handing criminals the keys to the entire castle. Purposely, the published exploit only worked if users disabled their browser’s sandbox, a sort of protective software cage that isolates the browser from the rest of the computer and protects it from exactly this kind of exploit. Criminals looking to use his exploit would have to chain it with a sandbox “escape”, a technically difficult task (although not an impossible one, as the Pwn2Own winners proved).
The update
The easiest way to do it is to allow Chrome to update automatically, which basically uses the same method as outlined below but does not require your attention. But you can end up lagging behind if you never close the browser or if something goes wrong, such as an extension stopping you from updating the browser.
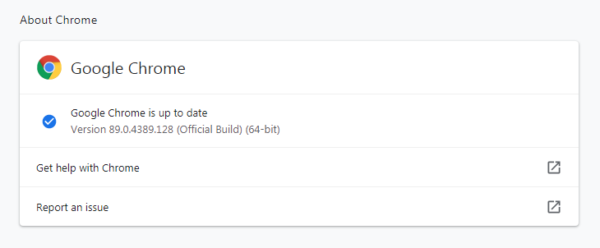
So, it doesn’t hurt to check now and then. And now would be a good time, given the working exploits. My preferred method is to have Chrome open the page chrome://settings/help which you can also find by clicking Settings > About Chrome.
If there is an update available, Chrome will notify you and start downloading it. Then it will tell you all you have to do to complete the update is Relaunch the browser.
Stay safe, everyone!
The post Update now! Chrome needs patching against two in-the-wild exploits appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![[HANDALA] - Ransomware Victim: Hotam EC 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)