URI spoofing flaw could phish WhatsApp, Signal, Instagram, and iMessage users
There’s a flaw in the way many of the world’s most popular messaging and email platforms—such as Facebook Messenger, Instagram, iMessage, Signal, and WhatsApp—render URIs (Uniform Resource Identifiers). That flaw makes it possible for phishing attempts to bypass filters and escape the trained eye, and results in apps incorrectly displaying URLs.
The flaw can be exploited when an attacker inserts an RTLO (right to left override) Unicode control character, which is used to display Arabic or Hebrew messages, in a string. Because messages written in these two languages are read from right to left, once the browser or messaging application sees the RTLO character, it displays every character after it right-to-left.
Two security researcher, zadewg and sick.codes, demonstrated this rendering flaw in a GitHub post you can see here.
“When a message contains a valid URL, it is highlighted and marked as hyperlink. However, this is printed to screen before sanitizing Unicode Control Characters, which results in URI spoofing via specially crafted messages.”
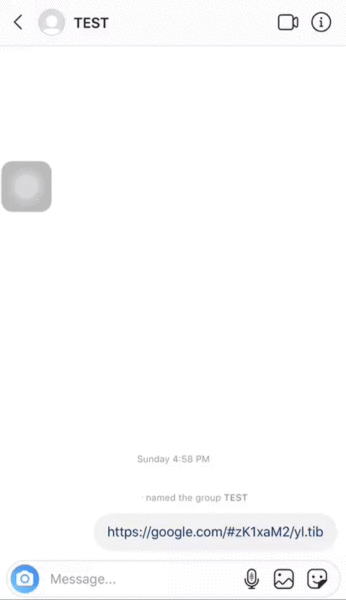
The two researchers used Google’s browser URL in a test case involving Instagram. In this case, they took https://google.com/ and combined it with the shortened URL, bit.ly/2Max1Kz#. They then inserted an RTLO Unicode character after the “/” of Google’s URL and before bit.ly. Once this is sent to someone, it will look like the URL you see on the GIF above:
https://google.com/#zK1xaM2/yl.tib
Notice that the bit.ly bit of the URL is flipped from the left-to-right orientation to the right-to-left orientation.
It’s simple to do, but what are the implications of this trick?
For one thing, it’s a tactic that attackers can use to fool potential victims by making them think what they received is legitimate. Attackers can piggyback on legitimate domains as well, such as in this demo where the domain is legitimately Google.
Abusing the RTL has been done many times in the past, but it usually involves filenames and not URLs. Several malware authors, such as those behind Bredolab, Mahdi, and SpyEye, are known to abuse the RTLO to hide malicious file names by disguising them as Word files or PDFs in spam attachments.
Malware Intelligence Researcher Pieter Arntz and Senior Security Researcher Jean Taggert have shown how the disguising could be done here and here, respectively. Sirefef, a Trojan known for its stealth, used RTLO when injecting malicious entries into the affected systems’ registry. And just last month, researchers from Vade Secure unearthed a phishing campaign that targeted Microsoft 365 users by disguising its spam attachment as a “voice message” when it was actually the phishing page in HTML format.
As there are a handful of applications affected by this flaw, each one has been assigned a CVE number to track:
- CVE-2020-20093 – Facebook Messenger 227.0 or prior for iOS and 228.1.0.10.116 or prior on Android
- CVE-2020-20094 – Instagram 106.0 or prior for iOS and 107.0.0.11 or prior on Android
- CVE-2020-20095 – iMessage 14.3 or older for iOS
- CVE-2020-20096 – WhatsApp 2.19.80 or prior for iOS and 2.19.222 or prior on Android
If you are wondering if the RTLO flaw works in emails, it doesn’t. BleepingComputer tested this on Gmail, Outlook.com, and Protonmail.
The URI spoofing flaw is still there with the current versions of Facebook Messenger, Instagram, iMessage, and WhatsApp. So, it’s best for users of these apps to exercise caution when clicking links until a patch or update is released for this flaw. Sick Codes has advised users the following:
“Turn off link previews in everything, especially mail apps and anything related to notifications. Don’t visit weird websites with popups. Don’t click random prize giveaways.
You already have a phone, so use your bookmarks and make sure to keep it up to date. Given the amount of zero-days flying around, especially those disclosed recently for iOS, it would be perilous to trust URLs in IMs.”
Stay safe!
The post URI spoofing flaw could phish WhatsApp, Signal, Instagram, and iMessage users appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[FLOCKER] - Ransomware Victim: G*********************y[.]org 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

