Vulnerability in DNS Servers Discovered By Academics from Israel

A vulnerability in DNS servers that can be exploited to launch DDoS attacks of huge extents was as of late discovered by a team academics from Israel, the attack as indicated by them impacts recursive DNS servers and the procedure of DNS delegation.
In a research paper published, the academics from the Tel Aviv University and The Interdisciplinary Center in Herzliya, Israel, said they figured out how to abuse this delegation procedure for DDoS attacks.
The NXNSAttack technique has various aspects and varieties, yet the fundamental steps are detailed below:
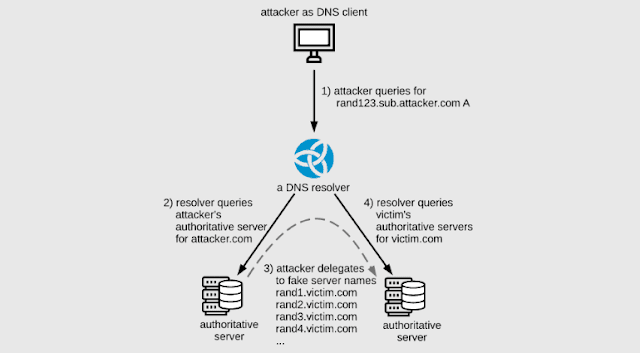
1) The attacker sends a DNS query to a recursive DNS server. The solicitation is for a domain like “attacker.com,” which is overseen through an attacker-controlled authoritative DNS server.
2) Since the recursive DNS server isn’t approved to resolve this domain, it forwards the operation to the attacker’s malicious authoritative DNS server.
3) The malignant DNS server answers to the recursive DNS server with a message that likens to “I’m delegating this DNS resolving operation to this large list of name servers.” The list contains a large number of subdomains for a victim website.
4) The recursive DNS server forwards the DNS inquiry to all the subdomains on the list, giving rise to a surge in traffic for the victim’s authoritative DNS server.
The Israeli researchers said they’ve been working for the past few months with the producers of DNS software; content delivery networks, and oversaw DNS suppliers apply mitigations to DNS servers over the world.
Affected software incorporates the likes of ISC BIND (CVE-2020-8616), NLnet labs Unbound (CVE-2020-12662), PowerDNS (CVE-2020-10995), and CZ.NIC Knot Resolver (CVE-2020-12667), yet additionally commercial DNS administrations provided by organizations like Cloudflare, Google, Amazon, Microsoft, Oracle (DYN), Verisign, IBM Quad9, and ICANN.
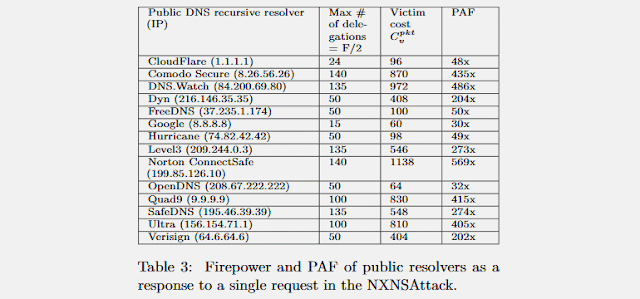
Patches have been discharged over the previous weeks. They incorporate mitigations that keep attackers from mishandling the DNS delegation procedure to flood different DNS servers.
The research team’s work has been properly detailed in a scholarly paper entitled “NXNSAttack: Recursive DNS Inefficiencies and Vulnerabilities,” available for download in PDF format.


