We found yet another phone with pre-installed malware via the Lifeline Assistance program
We have discovered, yet again, another phone model with pre-installed malware provided from the Lifeline Assistance program via Assurance Wireless by Virgin Mobile. This time, an ANS (American Network Solutions) UL40 running Android OS 7.1.1.
After our writing back in January—”United States government-funded phones come pre-installed with unremovable malware“—we heard an outcry from Malwarebytes patrons. Some claimed that various ANS phone models were experiencing similar issues to the UMX (Unimax) U683CL. However, it’s very hard to verify such cases without physically having the mobile device in hand. For this reason, I could not confidently write about such cases publicly. Thankfully, we had one Malwarebytes patron committed to proving his case. Thank you to Malwarebytes patron Rameez H. Anwar for sending us your ANS UL40 for further research! Your cyber-security expertise and persistence into this case will surely aid others!
Clarification of availability
To clarify, it is unclear if the phone in question, the ANS UL40, is currently available by Assurance Wireless. However, the ANS UL40 User Manual is listed (at the time of this writing) on the Assurance Wireless website.
Therefore, we can only assume it is still available to Assurance Wireless customers. Regardless, the ANS UL40 was sold at some point and some customers could still be affected.
Infection types
Just like the UMX U683CL, the ANS UL40 comes infected with a compromised Settings app and Wireless Update app. Although this may be true, they are not infected with the same malware variants. The infections are similar but have their own unique infection characteristics. Here’s a rundown of the infected apps.
Settings
- Package Name: com.android.settings
- MD5: 7ADA4AAEA49383499B405E4CE0A9447F
- App Name: Settings
- Detection: Android/Trojan.Downloader.Wotby.SEK

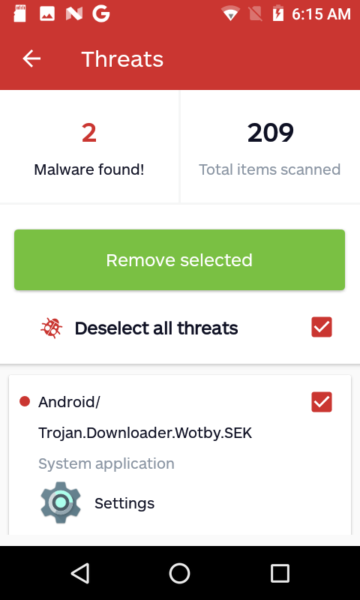
The Settings app is exactly what it sounds like—it is the required system app used to control all the mobile device’s settings. Thus, removing it would leave the device unusable. For the case of the ANS UL40, it is infected with Android/Trojan.Downloader.Wotby.SEK.
Proof of infection is based on several similarities to other variants of Downloader Wotby. Although the infected Settings app is heavily obfuscated, we were able to find identical malicious code. Additionally, it shares the same receiver name: com.sek.y.ac; service name: com.sek.y.as; and activity names: com.sek.y.st, com.sek.y.st2, and com.sek.y.st3. Some variants also share a text file found in its assets directory named wiz.txt. It appears to be a list of “top apps” to download from a third-party app store. Here’s snippet of code from the text file.
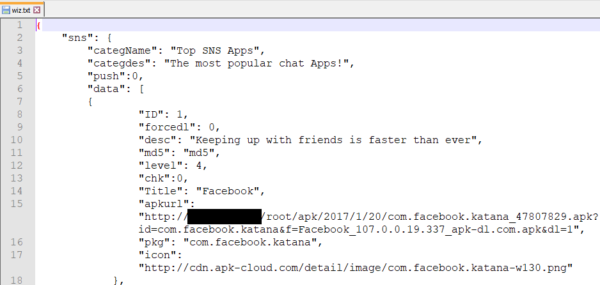
To be fair, no malicious activity triggered for us from this infected Settings app. We were expecting to see some kind of notification or browser popup populated with info from the code above displayed. Unfortunately, that never happened. But we also didn’t spend the normal amount of time a typical user would on the mobile device. Nor was a SIM card installed into the device, which could impact how the malware behaves. Nevertheless, there is enough evidence that this Settings app has the ability to download apps from a third-party app store. This is not okay. For this reason, the detection stands.
Although unsettling, it’s important to note that the apps from the third-party app store appear to be malware-free. This was verified by manually downloading a couple for ourselves for analysis. That’s not to say that malicious versions couldn’t be uploaded at a later date. Nor did we verify every sample. Nevertheless, we believe the sample set we did verify holds true for other apps on the site. Under those circumstances, even if the ANS’s Settings app had downloaded an app from the list, it’s still not as nefarious as the Settings app seen on the UMX U683CL.
WirelessUpdate
- Package Name: com.fota.wirelessupdate
- MD5: 282C8C0F0D089E3CD522B4315C48E201
- App Name: WirelessUpdate
- Detections: Three variants of Android/PUP.Riskware.Autoins.Fota
- Variants .INS, .fscbv, and .fbcv
WirelessUpdate is categized as a Potentially Unwanted Program (PUP) riskware auto-installer that has the ability to auto-install apps without user consent or knowledge. It also functions as the mobile device’s main source of updating security patches, OS updates, etc.
Android/PUP.Riskware.Autoins.Fota in particular is known for installing various variants of Android/Trojan.HiddenAds—and indeed it did! In fact, it auto installed four different variants of HiddenAds as seen below!
- Package Name: com.covering.troops.merican
- MD5: 66C7451E7C87AD5145596012C6E9F9A0
- App Name: Merica
- Detection: Android/Trojan.HiddenAds.MERI
- Package Name: com.sstfsk.cleanmaster
- MD5: 286AB10A7F1DDE7E3A30238D1D61AFF4
- App Name: Clean Master
- Detection: Android/Trojan.HiddenAds.BER
- Package Name: com.sffwsa.fdsufds
- MD5: 4B4E307B32D7BB2FF89812D4264E5214
- App Name: Beauty
- Detection: Android/Trojan.HiddenAds.SFFW
- Package Name: com.slacken.work.mischie
- MD5: 0FF11FCB09415F0C542C459182CCA9C6
- App Name: Mischi
- Detection: Android/Trojan.HiddenAds.MIS
Payload drop verification
Now you might be wondering, “How did you verify which of the two pre-installed infected system apps is dropping the payloads?” The process works as follows. You disable one of them upon initially setting up the mobile device. In both the UMX and ANS cases, picking which one to disable was easy to decide. That’s because disabling the Settings app renders the phone unusable. So, disabling WirelessUpdate was the obvious choice in both cases. The next step in the process is waiting a couple of weeks to see if anything happens. And yes, you sometimes need to wait this long for the malware to drop payloads. If nothing happens after a couple of weeks, then it’s time to re-enable the infected system app again and start the waiting game all over.
Using this process, we found in the case of the UMX U683CL, the Settings app was the culprit. For the ANS UL40, after not seeing any dropped payload(s) for weeks, I re-enabled WirelessUpdate. Within 24 hours, it installed the four HiddenAds variants! Caught red-handed, WirelessUpdate!
The tie between UMX and ANS
With our findings, we imagine some are left wondering: Is this a correlation or coincidence? We know that both the UMX and ANS mobile devices have the same infected system apps. However, the malware variants on the U683CL model and the UL40 are different. As a result, I initially didn’t think there was any ties between the two brands. I summed it up to be a coincidence rather than a correlation. That is until I stumbled upon evidence suggesting otherwise.
The Settings app found on the ANS UL40 is signed with a digital certificate with the common name of teleepoch. Searching teleepoch comes up with the company TeleEpoch Ltd along with a link to their website. Right there on the homepage of TeleEpoch Ltd it states, Teleepoch registered brand “UMX” in the United States.
Let’s review. We have a Settings app found on an ANS UL40 with a digital certificate signed by a company that is a registered brand of UMX. For the scoreboard, that’s two different Settings apps with two different malware variants on two different phone manufactures & models that appear to all tie back to TeleEpoch Ltd. Additionally, thus far the only two brands found to have preinstalled malware in the Settings app via the Lifeline Assistance program are ANS and UMX.
This led me to do further research into the correlation by looking at cases in our support system of other ANS models that might have preinstalled malware. That’s when I found the ANS L51. For the record, the L51 was another model being boasted as having preinstalled malware within the comments of the UMX article in January. I discovered that the ANS L51 had the same exact malware variants as the UMX U683CL! There, within previous support tickets, was hard proof of the ANS L51 infected with Android/Trojan.Dropper.Agent.UMX and Android/PUP.Riskware.Autoins.Fota.fbcvd. Driving home the triage of TeleEpoch, UMX, and ANS correlation!
Solutions
We have the utmost faith that ANS will quickly find a resolution to this issue. Just as UMX did as stated in the UPDATE: February 11, 2020 section of the January writing. As a silver lining, we did not find the Settings app on the ANS to be nearly as vicious as on the UMX. Thus, the urgency is not as severe this time around.
In the meantime, frustrated users with the ANS UL40 can halt the reinfection of HiddenAds by using this method to uninstall WirelessUpdate for current user (details in link below):
Removal instructions for Adups
Warning: Make sure to read Restoring apps onto the device (without factory reset) in the rare case you need to revert/restore app. For instance, if you like to restore WirelessUpdate to check if there are important system updates.
Use this/these command(s) during step 7 under Uninstalling Adups via ADB command line to remove:
adb shell pm uninstall -k –user 0 com.fota.wirelessupdate
Budget should not equate to malware
There are tradeoffs when choosing a budget mobile device. Some expected tradeoffs are performance, battery life, storage size, screen quality, and list of other things in order to make a mobile device light on the wallet.
However, budget should never mean compromising one’s safety with pre-installed malware. Period.
The post We found yet another phone with pre-installed malware via the Lifeline Assistance program appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



