Women Political Leaders Summit targeted in RomCom malware phishing
A new, lightweight variant of the RomCom backdoor was deployed against participants of the Women Political Leaders (WPL) Summit in Brussels, a summit focusing on gender equality and women in politics.
The campaign used a fake website mimicking the official WPL portal to bait people seeking to attend or simply interested in the summit.
A Trend Micro report analyzing the new variant warns that its operators, tracked by the firm as ‘Void Rabisu,’ have been using a stealthier backdoor with a new TLS-enforcement technique in the C2 (command and control) communications to make discovery harder.
Also, the latest attack cements the group’s shift from opportunistic ransomware attacks previously attributed to a Cuba ransomware affiliate to high-level cyberespionage campaign involving the exploitation of zero-day vulnerabilities in Microsoft products.
Targeting women political leaders
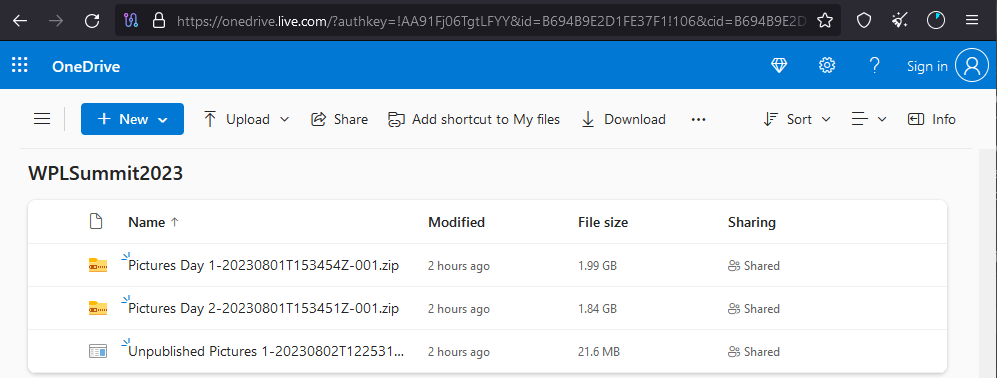
In August 2023, Void Rabisu set up a malicious website on the address ‘wplsummit[.]com’, designed to imitate the real Women Political Leaders (WPL) website hosted on wplsummit.org.

Source: Trend Micro
The fake site linked to a OneDrive folder through a button named ‘Videos & photos,’ which contained pictures from the two days of the event, taken from the genuine site, and a malware downloader named ‘Unpublished Pictures.’
The malicious executable is signed by an Elbor LLC certificate and is a self-extracting archive containing 56 photos to act as decoys, while a second encrypted file is downloaded from a remote host.
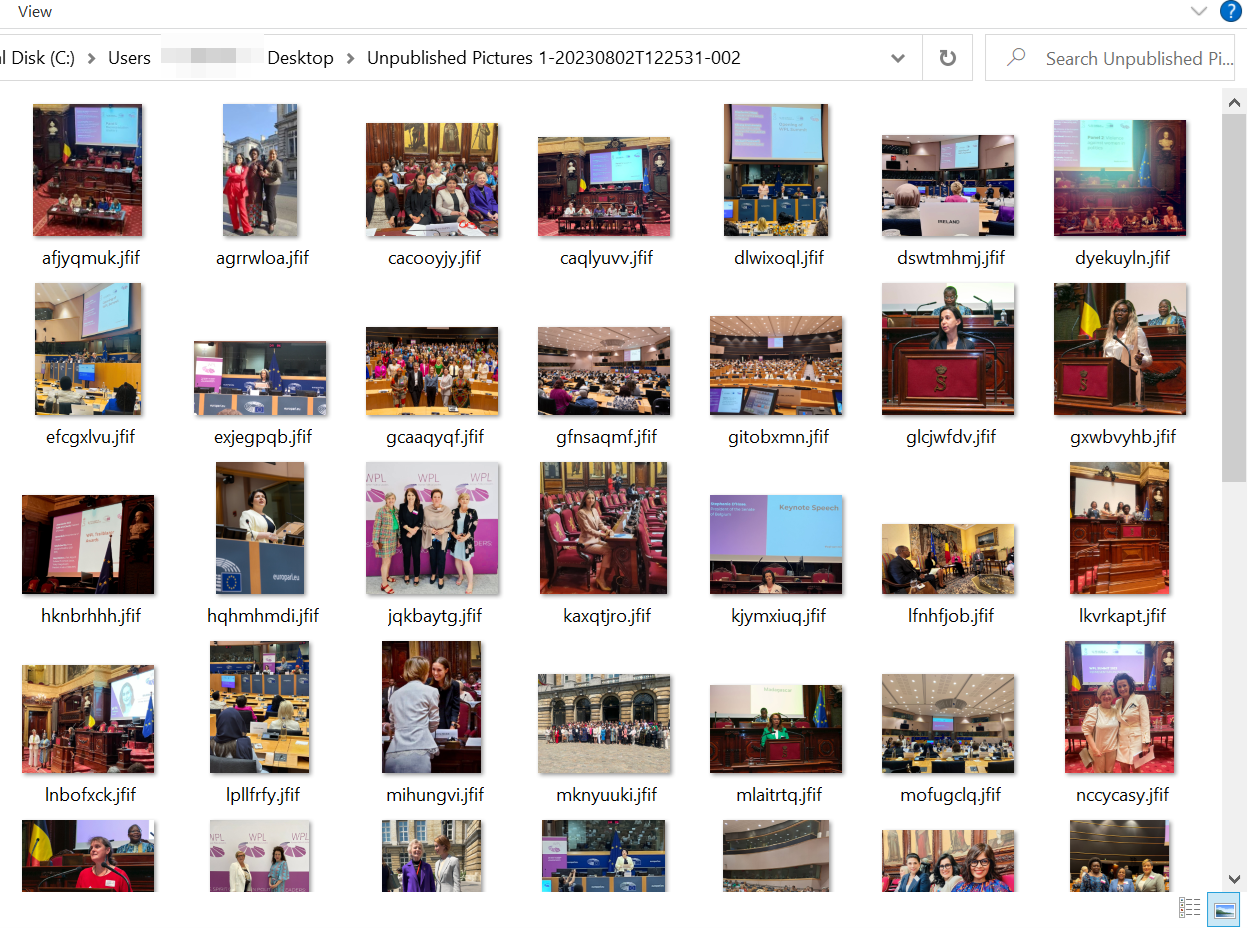
Source: Trend Micro
The second payload is a DLL that is decrypted and loaded into memory to evade detection and continues to fetch additional components required for establishing communication with the attacker’s server.
Source: Trend Micro
RomCom 4.0
Trend Micro identifies the latest, stripped-down variant of RomCom as the fourth major release of the backdoor, explaining that it’s the same malware Volexity researchers recently named ‘Peapod.’
Compared to RomCom 3.0, the previous version seen in Void Rabisu operations, the new backdoor variant has undergone significant changes, making it lighter and stealthier.
It now supports only the following ten commands, a stark reduction from the previous 42.
- No action – Handling function returns zero; malware waits for the next command.
- Run command – Executes a command and sends back its output.
- Upload file – Uploads a file to the compromised machine.
- Download file – Retrieves a file from the infected machine.
- Run command – Executes a given command.
- Update interval – Modifies backdoor check frequency (default 60 seconds) and updates the system registry.
- Get system info – Retrieves RAM, processor, local time, and username.
- Update network component – Updates data for the network component in the Windows registry.
- Uninstall – Purges relevant registry keys and deletes associated files.
- Get service name from the Windows registry
Also, instead of utilizing modified MSIs to drop its components onto devices directly, the new variant leverages an EXE file to fetch XOR-encrypted DLLs, loading all its components in memory.
RomCom 4.0 has also incorporated new features related to Transport Layer Security (TLS), a protocol designed to provide secure communication with the C2 server.
The malware has been coded to force WinHTTP functions to specifically use the TLS version 1.2 rather than allowing the operating system to choose the default TLS version.
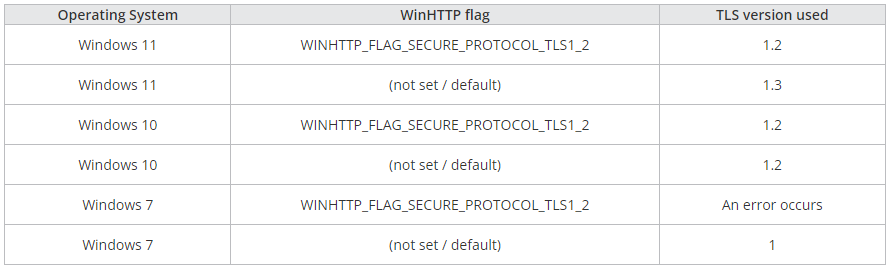
Source: Trend Micro
This enforcement system results in an error on Windows 7, which Trend Micro considers safe against the newest RomCom variant.
The goal of this mechanism is likely to make C2 communication more resistant to snooping, complicate automated discovery, and possibly allow attackers to filter out unsuitable victims.
In general, Void Rabisu’s tactics and the deployment of the RomCom malware remain cloudy.
However, it is clear that the backdoor’s development is still ongoing, and its operators are increasingly focused on top-level cyber espionage.
Trend Micro concludes that it is very likely that Void Rabisu will target all big conferences related to special interest groups, so caution is advised when visiting event sites.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


