You have around 20 minutes to contain a Russian APT attack
Governments and private organisations have around 20 minutes to detect and contain a hack from Russian nation-state actors.
New statistics published today by US cyber-security firm Crowdstrike ranked threat groups based on their “breakout time.”
“Breakout time” refers to the time a hacker group takes from gaining initial access to a victim’s computer to moving laterally through its network. This includes the time the attacker spends scanning the local network and deploying exploits in order to escalate his access to other nearby computers.
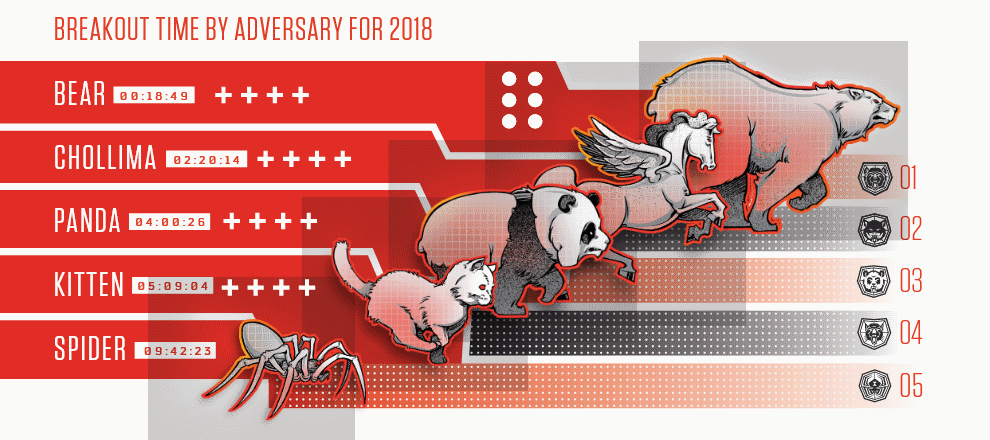
According to data gathered from 2018 hack investigations, CrowdStrike says Russian hackers (which the company calls internally “Bears”) have been the most prolific and efficient hacker groups last year,
Russia “Bears” top the charts with an average breakout time of 18 minutes and 49 seconds.
They’re followed by North Korean groups (Chollimas) with two hours and 20 minutes,
Chinese hacker groups (Pandas) with four hours,
Iranians (Kittens) with five hours and nine minutes,
and cybercrime gangs (Spiders) with roughly nine hours and 42 minutes.
“The overall average breakout time that CrowdStrike observed in 2018 across all intrusions and threat actors was 4 hours 37 mins, a substantial increase from 1 hour and 58 minutes tracked in 2017,” the CrowdStrike team said.
“While certainly not the only metric to judge sophistication by, this ranking by breakout time is an interesting way to evaluate the operational capabilities of major threat actors,” they added.
The ability to break out of an initially compromised computer takes both skill and readily available hacking tools and exploits. It is only normal that Russian, North Korean, and Chinese groups rank high on this ranking, as they’ve been the most active cyber threat actors over the past decade, putting years of work into building advanced tools and honing their skills.


