BlackHat Europe 2016: Day 1 of 2
Today was day 1 of 2 for me at BlackHat Europe 2016, one of my highlights was the tool Bloodhound located in the Arsenal section.
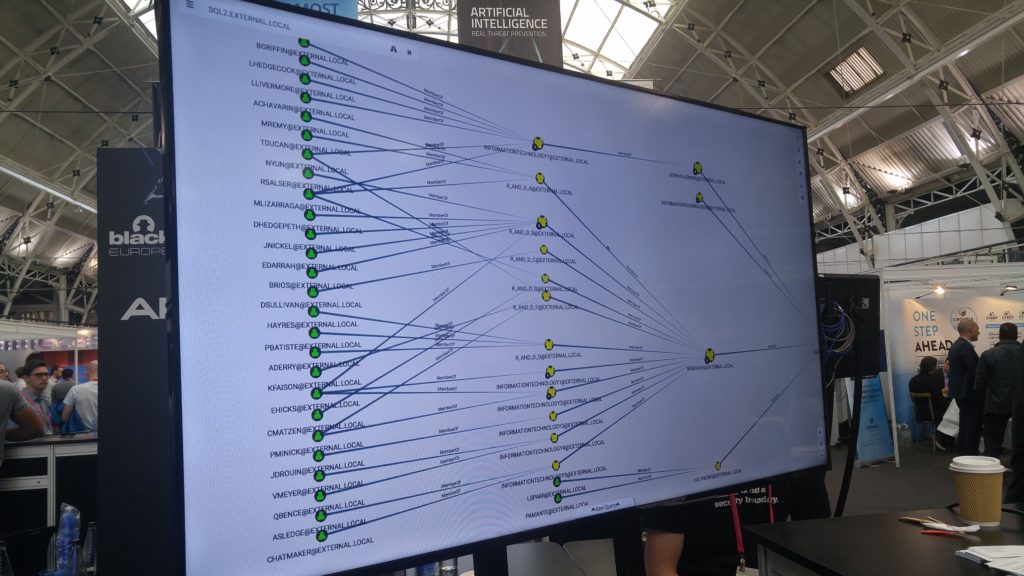
BloodHound uses graph theory to reveal hidden relationships and attack paths in an Active Directory environment. Basically it shows the quickest way to get domain admin.
Active Directory domain privilege escalation is a critical component of most penetration tests and red team assessments, but standard methodology dictates a manual and often tedious process – gather credentials, analyze new systems we now have admin rights on, pivot, and repeat until we reach our objective. Then – and only then – we can look back and see the path we took in its entirety. But that may not be the only, nor shortest path we could have taken.
Otherwise invisible, high-level organizational relationships are exposed. Most possible escalation paths can be efficiently and swiftly identified. Simplified data aggregation accelerates blue and red team analysis. BloodHound has the power and the potential to dramatically change the way you think about and approach Active Directory domain security.
The great thing about it is, as a defender we can use this tool also before an attacker and try to clean up some of this mess and reduce the amount of lateral movement across the domain.
It’s free and easy to use, what’s not to like?
Another one of the interesting briefings was the below talk about WAFs and how to bypass them,
Web Applications Firewalls (WAFs) are fundamental building blocks of modern application security. For example, the PCI standard for organisations handling credit card transactions dictates that any application facing the internet should be either protected by a WAF or successfully pass a code review process. Nevertheless, despite their popularity and importance, auditing web application firewalls remains a challenging and complex task. Finding attacks that bypass the firewall usually requires expert domain knowledge for a specific vulnerability class. Thus, penetration testers not armed with this knowledge are left with publicly available lists of attack strings, like the XSS Cheat Sheet, which are usually insufficient for thoroughly evaluating the security of a WAF product.
Using a tool called Lightbulb as discussed in the talk is a way to start using automata learning algorithms can be used to obtain useful models of WAFs. Using this technique they found over 10 previously unknown vulnerabilities in popular WAFs such as Mod-Security, PHPIDS and Expose allowing us to mount SQL Injection and XSS attacks bypassing the firewalls. Complicated to understand the algorithm but very interesting nevertheless.

And then there was lunch! 2 meatballs only! C’mon need to do better than that 😉

But there was plenty of swag to be had, so I’ll let the meatballs slide!

Interesting to see what tomorrow brings!


