BlackHat Europe 2016: Day 2 of 2
Day 2 at Blackhat EU 2016 and had a great day.
This talk Breaking Big Data: Evading Analysis of the Metadata of Your Life was very interesting by a former NSA professional talking about a variety of the techniques used by the mass surveillance industry to analyse an individual’s metadata and develop a profile of you, your activities, your affiliations, and what you are likely to buy next. Techniques that can be used to prevent selected activities from being associated with your true persona will be covered, with a focus on making your true persona blend in with the masses.
You are under surveillance. We all are. If you’re targeted by a government, nothing you can do will save you. But even if you aren’t, the metadata of your life is being gathered and stockpiled by collection capabilities that even Orwell couldn’t have imagined, and it’s not just being done by governments. The big data industry is rapidly growing and may soon be on par with NSA-style mass surveillance, but with a different goal: to learn everything they can about you in order to sell your information, and sell you the next new thing.

Encryption is only half the battle. Your metadata is often more valuable than your data. Every route you drive, every social media post you make, every aisle you visit in the grocery store, every email, every check-in, and every site you browse is being collected and correlated. The intelligence community calls this pattern-of-life analysis, and there’s not much you can do to prevent it. Hiding behind seven proxies won’t protect you from Google, the NSA, or the app on your phone with global permissions. This complete erosion of privacy impacts every one of us, and there is a complete lack of transparency around this.

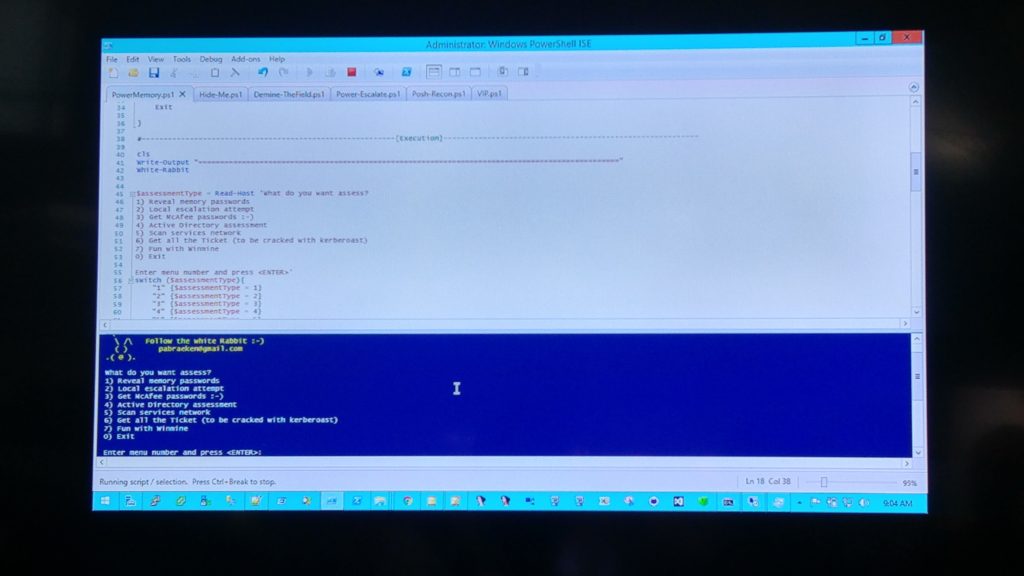
Moving over to the Arsenal, one of the tools i really liked was PowerMemory.
PowerMemory is a PowerShell post-exploitation tool. It uses Microsoft binaries and therefore is able to execute on a machine, even after the Device Guard Policies have been set. In the same way, it will bypass antivirus detection. PowerMemory can retrieve credentials information and manipulate memory. It can execute shellcode and modify process in memory (in userland and kernel land as a rootkit). PowerMemory will access everywhere in user-land and kernel-land by using the trusted Microsoft debugger aka cdb.exe which is digitally signed.
This is some really cool stuff and it never touched the HDD 🙂 nice!
Back to the Briefing’s and we are looking at some OBD-II and UDS hacking with CANToolz.
CANToolz is an open-source framework for working with CAN bus which is basically the LAN in a car. The author was demonstrating use-cases and examples of black-box analyses of CAN network and ECU devices.

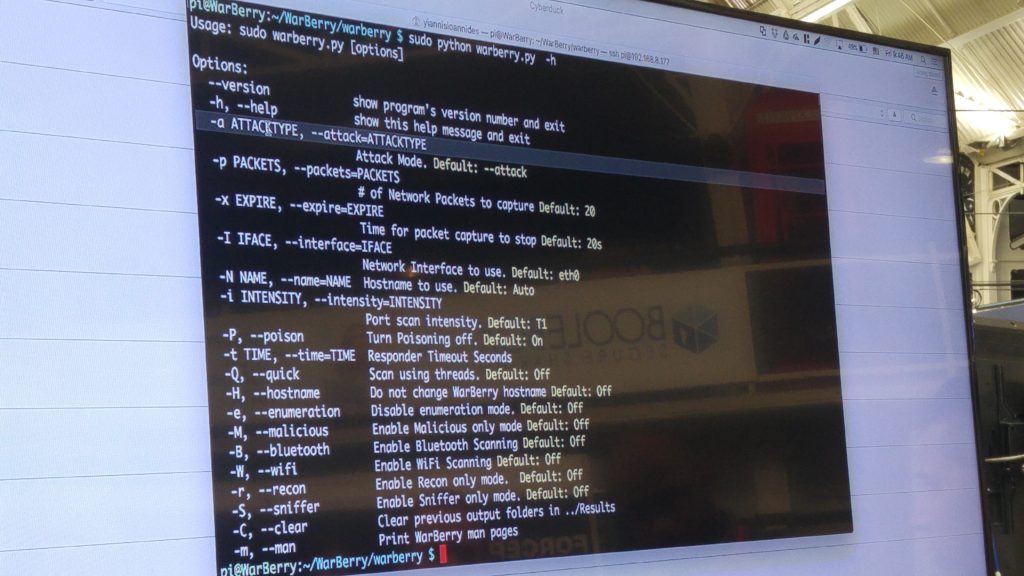
WarberryPi
What if the only requirements for taking down a corporate network are 60 minutes and $35? Traditional hacking techniques and corporate espionage have evolved. Advanced attacks nowadays include a combination of social engineering, physical security penetration and logical security hacking. It is our job as security professionals to think outside the box and think about the different ways that hackers might use to infiltrate corporate networks.
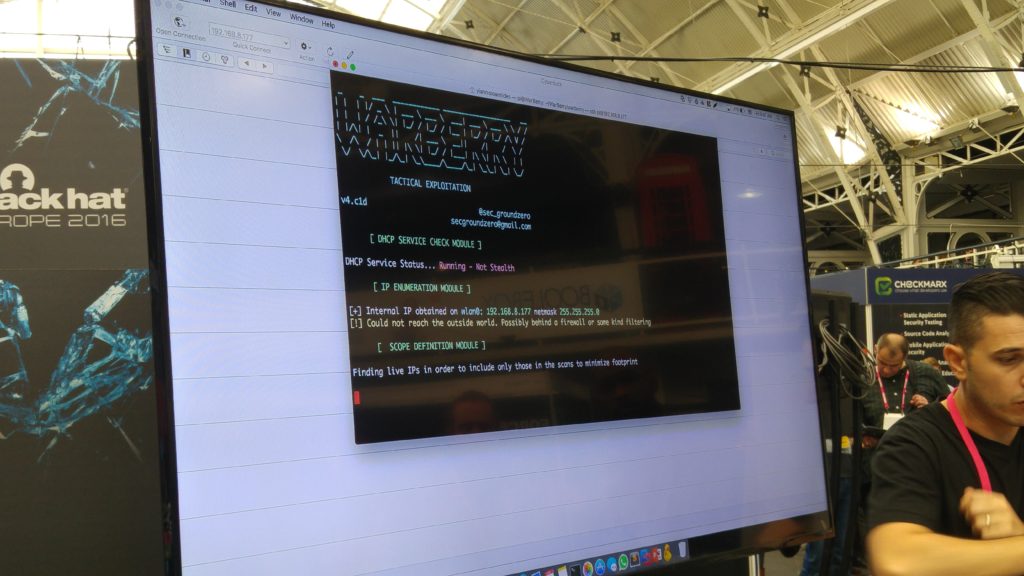
The WarBerry is a customized RaspBerryPi hacking dropbox which is used in Red Teaming engagements with the sole purpose of performing reconnaissance and mapping of an internal network and providing access to the remote hacking team while remaining covert and bypassing security mechanisms. The outcome of these red teaming exercises is the demonstration that if a low cost microcomputer loaded with python code can bypass security access controls and enumerate and gather such a significant amount of information about the infrastructure network which is located at, then what dedicated hackers with a large capital can do is beyond conception. The talk will be comprised of slides and a demonstration of the WarBerry’s capabilities in a virtual network.
When serious vulnerabilities like ShellShock or ImageTragick are revealed, the announcement is often accompanied by PoC code. But what are the real payloads that attackers attempt to use when exploiting these vulnerabilities? Seeing the real payloads people use is often very difficult, but CloudFlare is in a unique position. By offering security services to over 4 million websites and detecting the exploitation of vulnerabilities like ShellShock or ImageTragick, they are able to see the actual payloads that attackers are using.

This talk was quite interesting in seeing what attackers are attempting to use in regards to exploits , some old some new and very interesting.

![[QILIN] - Ransomware Victim: Mainetti 9 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

