D.C. Board of Elections: Hackers may have breached entire voter roll

The District of Columbia Board of Elections (DCBOE) says that a threat actor who breached a web server operated by the DataNet Systems hosting provider in early October may have obtained access to the personal information of all registered voters.
The entire voter roll that may have been exposed contains a wide range of personally identifiable information (PII), including driver’s license numbers, dates of birth, partial social security numbers, and contact information such as phone numbers and email addresses.
“Today, DCBOE learned the full voter roll MAY have been accessed in the breach of DataNet Systems’ database server,” the agency tweeted.
“DataNet Systems could not pinpoint if or when this file may have been accessed or how many, if any, voter records were accessed,” DCBOE said in a Friday update.
“Out of an abundance of caution, DCBOE will reach out to all registered voters. In addition, DCBOE will be engaging with Mandiant, a cybersecurity consulting firm, to assist with next steps.”
Website breach leads to voter data leak
On October 5, 2023, the DCBOE became aware of a breach involving a threat actor known as RansomVC, which claimed to have stolen 600,000 lines of U.S. voter data, including D.C. voter records.
In collaboration with MS-ISAC’s Computer Incident Response Team (CIRT), the agency took down its website upon discovering the attack. They replaced it with a maintenance page to contain the situation after identifying the website as the source of the breach.
Further investigations revealed the attackers gained access to the information through the web server of DataNet, the hosting provider for Washington D.C.’s election authority. No DCBOE databases or servers were directly compromised in the incident.
The DCBOE is investigating the breach with the assistance of external security experts, the Federal Bureau of Investigation (FBI), and the Department of Homeland Security (DHS).
The efforts are focused on assessing the full extent of the breach, identifying the vulnerabilities exploited during the attack, and implementing measures to safeguard voter data and systems.
Stolen data up for sale
On their dark web website, RansomedVC claims the recent security breach led to the theft of more than 600,000 lines of voter data from the United States.
“We have successfully penetrated the District of Columbia Board Of Elections and have acquired over 600k lines of USA Voters,” says the threat actor.
RansomedVC says the stolen data contains Washington D.C. voters’ personal information, including names, registration IDs, voter IDs, partial Social Security numbers, driver’s license numbers, dates of birth, phone numbers, emails, and more.
The information is still available for sale on the threat actor’s dark web leak site, although the price remains undisclosed.
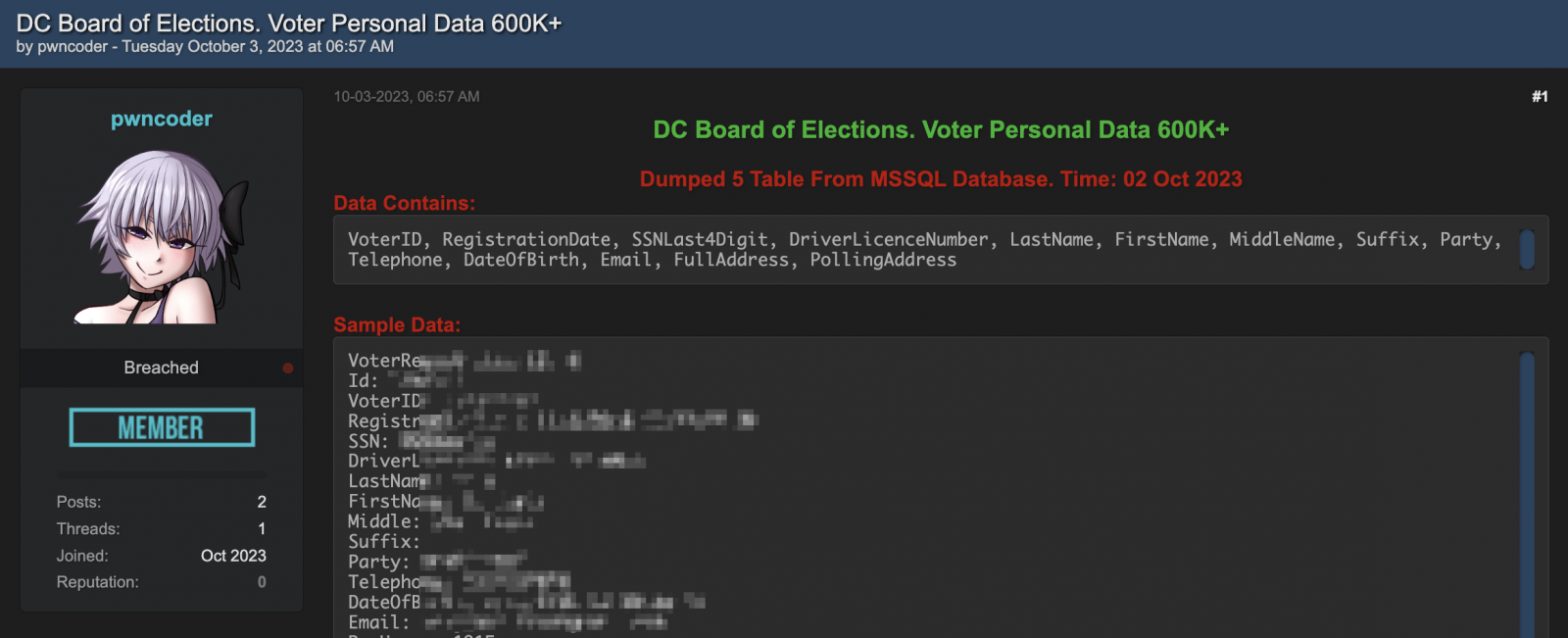
Despite RansomedVC’s claim of the breach and their current attempt to sell the data on their leak site, an anonymous source told BleepingComputer was told on October 3 that the stolen DCBOE database was first offered for sale on the BreachForums and Sinister.ly hacking forums by a user named pwncoder.
It is worth noting that both those posts have since been removed, and RansomedVC is the only threat actor still selling the data.
BleepingComputer was also told that the data was extracted from a stolen MSSQL database containing the details of more than 600,000 voters from the District of Columbia.
Recent claims made by RansomedVC to have hacked into Sony’s servers and stolen over 260GB of files (with a 2MB leaked archive shared as proof) were also challenged by another threat actor known as MajorNelson, who released a 2.4 GB archive of files on BreachForums, also allegedly taken from Sony’s systems.
Although the data they shared appears to be associated with Sony, BleepingComputer could not independently confirm the authenticity of the claims made by either party.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[INCRANSOM] - Ransomware Victim: C B King Memorial School(branch) 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)



