Malicious Solana, Kucoin packages infect NuGet devs with SeroXen RAT

Malicious NuGet packages appearing to have over 2 million downloads impersonate crypto wallets, crypto exchange, and Discord libraries to infect developers with the SeroXen remote access trojan.
NuGet is an open-source package manager and software distribution system that operates package hosting servers to enable users to download and use them for their development projects.
The malicious packages uploaded on NuGet by a user named ‘Disti’ were discovered by Phylum researchers, who published a report today to warn about the threat.
Inflated authenticity
All six packages in Disti’s repository contain the same XML file that downloads ‘x.bin,’ an obfuscated Windows batch file that carries out malicious activities on the compromised system.
The packages mimic popular cryptocurrency projects, exchanges, and platforms, even featuring the official logos to trick users.
The six packages uploaded by Disti on NuGet, and which are still available at the time of writing, are:
- Kraken.Exchange – 635k downloads
- KucoinExchange.Net – 635k downloads
- SolanaWallet – 600k downloads
- Modern.Winform.UI – 100k downloads
- Monero – 100k downloads
- DiscordsRpc – 75k downloads
The download numbers are believed to be inflated and may not be representative of the reach of these packages in the NuGet community.
Still, these download counts effectively enhance the perceived credibility of the packages, making them seem like genuine versions of the apps or platforms implied by their names.
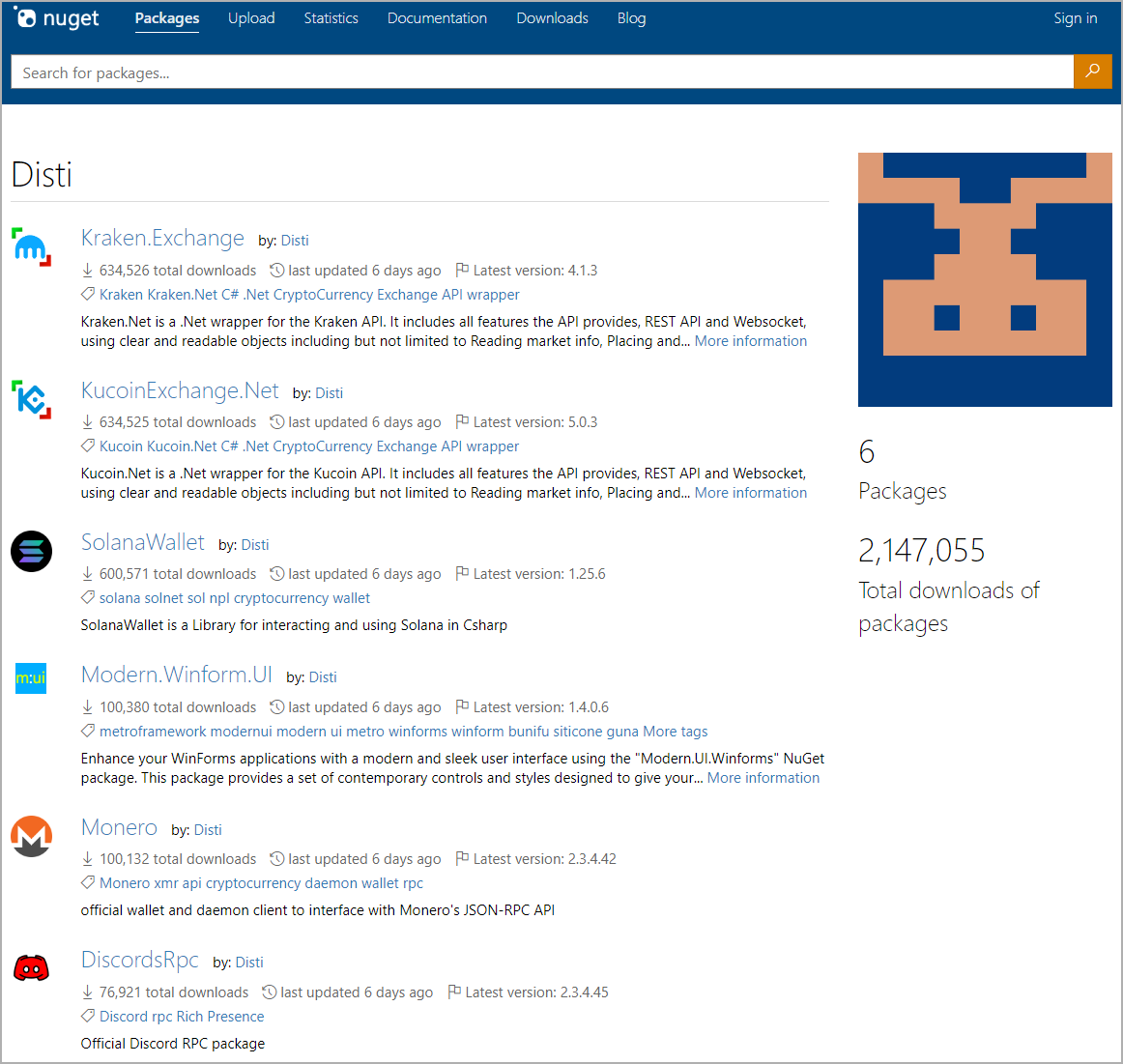
Disti might have inflated the download figures using automated scripts, botnets, virtual machines, or cloud containers that download a package many times.
The SeroXen RAT
The packages incorporate two PowerShell scripts that execute CMD and Batch files during installation on the victim’s computer.
The script downloads a file from an external URL, saves it as “.cmd” on a temp directory, and executes it without displaying anything on the screen.
This script fetches another file named ‘x.bin,’ which, despite its name, is an obfuscated batch script with over 12,000 lines, and its purpose is to construct and execute yet another PowerShell script.
Eventually, that final script reads portions from the cmd file to decrypt and decompress an encoded payload from within itself, which Phylum says is SeroXen RAT.
This feature-rich remote access trojan is marketed as a legitimate program and sold for $15/month or a single “lifetime” purchase of $60.
In May, AT&T reported that SeroXen RAT is gaining popularity among cybercriminals who value its low detection rates and powerful capabilities.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[LYNX] - Ransomware Victim: Greta Group 4 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
