Ransomware attacks now target unpatched WS_FTP servers

Internet-exposed WS_FTP servers unpatched against a maximum severity vulnerability are now targeted in ransomware attacks.
As recently observed by Sophos X-Ops incident responders, threat actors self-described as the Reichsadler Cybercrime Group attempted, unsuccessfully, to deploy ransomware payloads created using a LockBit 3.0 builder stolen in September 2022.
“The ransomware actors didn’t wait long to abuse the recently reported vulnerability in WS_FTP Server software,” Sophos X-Ops said.
“Even though Progress Software released a fix for this vulnerability in September 2023, not all of the servers have been patched. Sophos X-Ops observed unsuccessful attempts to deploy ransomware through the unpatched services.”
The attackers attempted to escalate privileges using the open-source GodPotato tool, which allows privilege escalation to ‘NT AUTHORITY\SYSTEM’ across Windows client (Windows 8 to Windows 11) and server (Windows Server 2012 to Windows Server 2022) platforms.
Fortunately, their attempt to deploy the ransomware payloads on the victim’s systems was thwarted, preventing the attackers from encrypting the target’s data.
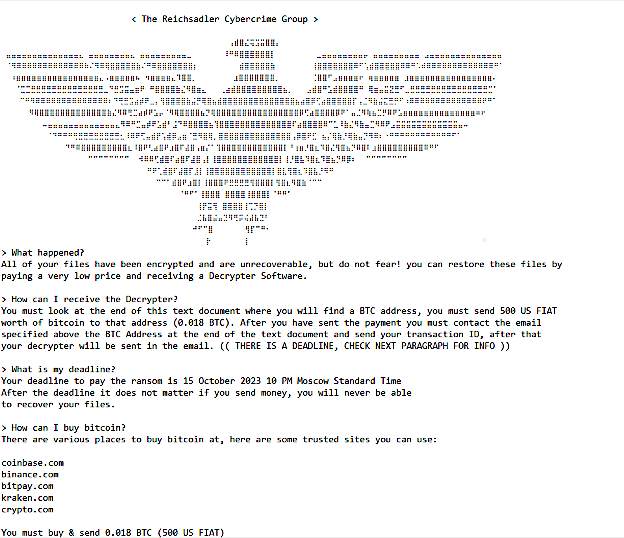
Even though they failed to encrypt the files, the threat actors still demanded a $500 ransom, payable by October 15, Moscow Standard Time.
The low ransom demand hints at Internet-exposed and vulnerable WS_FTP servers likely being targeted in mass automated attacks or by an inexperienced ransomware operation.
Tracked as CVE-2023-40044, the flaw is caused by a .NET deserialization vulnerability in the Ad Hoc Transfer Module, enabling unauthenticated attackers to execute commands on the underlying OS via HTTP requests remotely.
On September 27, Progress Software released security updates to address the critical WS_FTP Server vulnerability, urging admins to upgrade vulnerable instances.
“We do recommend upgrading to the most highest version which is 8.8.2. Upgrading to a patched release, using the full installer, is the only way to remediate this issue,” Progress said.
Assetnote security researchers who discovered the WS_FTP bug released proof-of-concept (PoC) exploit code just days after it was patched.
“From our analysis of WS_FTP, we found that there are about 2.9k hosts on the internet that are running WS_FTP (and also have their webserver exposed, which is necessary for exploitation). Most of these online assets belong to large enterprises, governments and educational institutions,” Assetnote said.
Cybersecurity company Rapid7 revealed that attackers began exploiting CVE-2023-40044 on September 3, the day the PoC exploit was released.
“The process execution chain looks the same across all observed instances, indicating possible mass exploitation of vulnerable WS_FTP servers,” Rapid7 warned.
Shodan lists almost 2,000 Internet-exposed devices running WS_FTP Server software, confirming Assetnote’s initial estimates.
Organizations that cannot immediately patch their servers can block incoming attacks by disabling the vulnerable WS_FTP Server Ad Hoc Transfer Module.
The Health Sector Cybersecurity Coordination Center (HC3), U.S. Health Department’s security team also warned Healthcare and Public Health sector organizations last month to patch their servers as soon as possible.
Progress Software is currently dealing with the aftermath of a widespread series of data theft attacks that exploited a zero-day bug in its MOVEit Transfer secure file transfer platform earlier this year.
These attacks impacted over 2,500 organizations and more than 64 million individuals, as estimated by Emsisoft.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.


