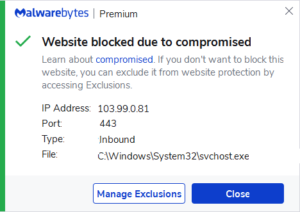
United States Charged Six Russian Intelligence Officers with Involvement in An Unrestricted Huge Hacking Campaign
With involvement in an 'unrestricted huge hacking campaign', which incorporates the famous Petya ransomware attacks which have focused mainly...