Patch Tuesday – October 2020

Microsoft brings us an October’s Update Tuesday with 87 vulnerabilities, a sub-100 number we haven’t experienced in quite some time. To further add to this oddity, there are no Browser-based vulnerabilities to mention and the arrival of a new Adobe Flash vulnerability CVE-2020-9746. Despite this month’s lower numbers, there are some precautions we should all take to remediate our environments quickly and effectively.
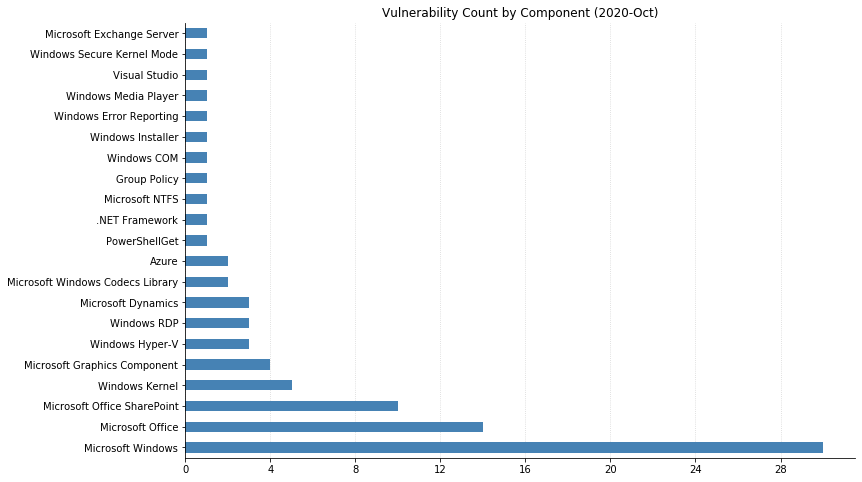
Starting with Microsoft Windows
As usual, whenever possible, it’s better to prioritize updates against the Windows operating system. Coming in at 53 of the 87 vulnerabilities, patching the OS knocks out 60% of the vulnerabilities listed along with over half of the critical remote code execution vulnerabilities resolved today.
Microsoft CVE-2020-16898: Microsoft TCP/IP Remote Code Execution Vulnerability
With a CVSS score of 9.8 and marked as “Exploitation More Likely”, this vulnerability grants the ability to execute code on target Windows 10 (version 1709+), Windows Server 2019, and Windows Server version 1903+ systems due to improper handling of ICMPv6 Router Advertisement packets.
Luckily, if immediate patching isn’t viable due to reboot scheduling, Microsoft provides PowerShell-based commands to disable ICMPv6 RDNSS on affected operating systems. The PowerShell command netsh int ipv6 set int *INTERFACENUMBER* rabaseddnsconfig=disable does not require a reboot to take effect.
Microsoft CVE-2020-16896: Windows Remote Desktop Protocol (RDP) Information Disclosure Vulnerability
RDP has been a focal point for some of recent attacks (e.g. BlueKeep), so whenever Microsoft provides another fix within that realm, it’s prudent to make note of some specifics. CVE-2020-16896 is an information disclosure vulnerability where, when successfully exploited, allows unauthorized read access to the Windows RDP server process.
This RDP vulnerability, like previous ones of late, affects all supported Windows operating systems, and can continue to be mitigated by practices such as enabling Network Level Authentication (NLA) or by blocking TCP port 3389 at the enterprise perimeter firewall.
Microsoft CVE-2020-16911: GDI+ Remote Code Execution Vulnerability
Critical remote code execution vulnerability CVE-2020-16911 leverages how the Windows Graphics Device Interface (GDI) handles objects in memory. A successful exploitation allows the attacker to install programs and/or create new accounts under the same user rights as the user who triggered this vulnerability.
A mitigating factor here is that users with fewer privileges on the system could be less impacted, but still emphasizes the importance of good security hygiene as exploitation requires convincing a user to open a specially-crafted file or to view attacker-controlled content.
Unlike CVE-2020-16898, however, this vulnerability affects all supported versions of Windows OS, which may suggest affecting unsupported/earlier versions of Windows as well.
Moving on to Microsoft SharePoint
Continuing last month’s trend, there are more SharePoint-related vulnerabilities being addressed this month (10 of them) than past months. If relevant in your environment, the respective KBs for your version of SharePoint should be the next batch of patches to prioritize. Below are some highlights of the higher CVSS-scored ones.
Microsoft SharePoint Remote Code Execution Vulnerabilities (CVE-2020-16951, CVE-2020-16952)
With Proof-of-Concept exploits starting to flow out in the wild, bringing a closure to this pair of critical remote code execution vulnerabilities is a must.
CVE-2020-16951 and CVE-2020-16952 are remote code execution vulnerabilities that exploit a gap in checking the source markup of an application package. Upon successful exploitation, the attacker could run arbitrary code in the context of the SharePoint application pool or server farm account.
For more in-depth attacker perspective, visit AttackerKB’s take on CVE-2020-16952.
Microsoft SharePoint Reflective XSS Vulnerabilities (CVE-2020-16944, CVE-2020-16945, CVE-2020-16946)
The last set of notable SharePoint vulnerabilities this month are three CVSS 8.7 spoofing vulnerabilities. Requiring a user to click a specially-crafted URL within targeted SharePoint Web App site, a successful exploitation from those means allows the attacker to perform cross-site scripting attacks and/or run scripts in the security context of the user.
Closing October’s Update Tuesday journey with Microsoft Office
While we always expect Office-based vulnerabilities every month, two vulnerabilities particularly stood out. In both cases, the Preview Pane is considered an attack vector, which lowers the barriers to entry a bit.
Microsoft CVE-2020-16947: Outlook Remote Code Execution Vulnerability
A critical remote code execution vulnerability for Outlook 2016, Office 2019 and Microsoft 365 apps only, CVE-2020-16947 has the potential to allow an attacker to run arbitrary code in the context of the user. The attacker could then install programs or create new accounts with full user rights.
While the details behind this vulnerability feels standard from Microsoft’s description, it actively acknowledges that the Preview Pane is an attack vector, and that in itself, attracts some attention.
Microsoft CVE-2020-16949: Outlook Denial of Service Vulnerability
CVE-2020-16949 is an Outlook vulnerability that affects more versions than the list around CVE-2020-14947 including Outlook 2010 and Outlook 2013. This vulnerability, however, reads differently in that this denial of service vulnerability only requires that a specially-crafted email be sent. When paired with the fact that this vulnerability is marked with the Preview Pane as an attack vector, just like CVE-2020-16947, suggests giving Outlook its fair share of attention this month.
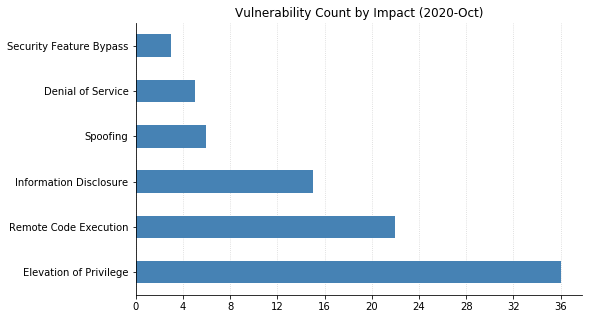
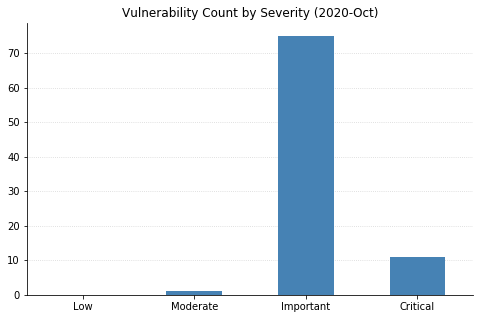
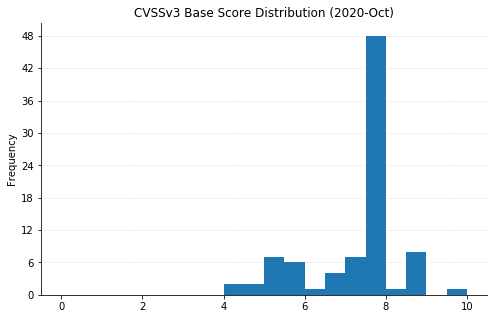
Note: Graph data is reflective of data presented by Microsoft’s CVRF at the time of writing.
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



