2021 Detection and Response Planning, Part 2: Driving SOC Efficiency With a Detections-First Approach to SIEM

This is the second installment of our series around 2021 security planning. In part one, Rapid7 Detection and Response Practice Advisor Jeffrey Gardner offered tips and advice for ramping up annual security planning. In this installment, we’ll explore the importance of reliable and comprehensive detections to drive an efficient security program forward.
As we started to get into in the first installment, teams are under tremendous pressure to demonstrate progress and ROI, which means they need to find efficient ways to optimize and advance security without adding more complexity. Too many legacy and traditional SIEM approaches actually introduce more work for teams and distract from actual detection and response. Teams get bogged down in arduous deployments, writing and managing rules, and jumping among various datasets to try to build a complete picture. For this reason, too many tools end up partially deployed or full on shelfware, leaving teams burnt out and environments exposed.
See How Modern SIEM Solutions Drive Immediate Value
Learn More
Security Planning Tip: Shelfware is the nemesis of ROI. When you’re doing security planning and evaluating new tools, think about what deploying and actually achieving your desired outcomes would require. Do you have the staff, time, resources to get to your end goals with the product you’re evaluating? If the answer is “no” or “not sure,” it might be time to look at something else.
Rapid7’s approach to security information and event management (SIEM) is unique in that we have focused on a detections-first mindset. InsightIDR, our leading SaaS SIEM, provides a growing library of pre-built detections out of the box. Where other tools may give users centralized data and leave it up to them to figure out how to turn that into detections, InsightIDR provides reliable detections, then provides the additional context and information to do something about it. This, along with our lightweight, software-based deployment, rapidly accelerates setup and value realization for customers. In fact, per our Total Economic Impact study, InsightIDR customers are up and running in less than a month and a half and typically start seeing a return on their investment in less than three months.
A multi-layered approach to detection and response
Detections are only useful when they are reliable and actionable, which is why InsightIDR’s approach to detections is multifaceted.
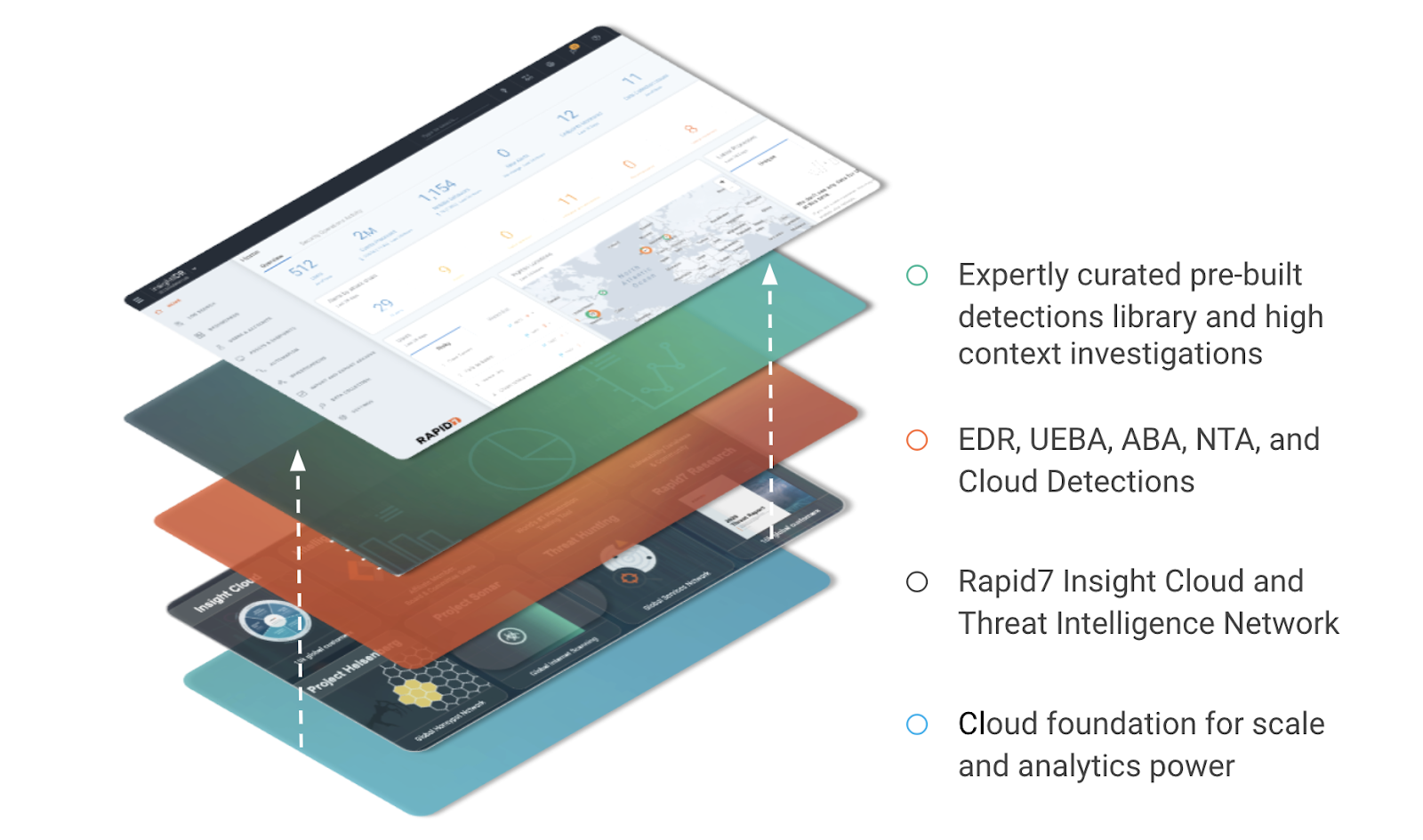
Get the horsepower necessary to monitor modern environments with InsightIDR’s cloud foundation
As Jon Oltsik, principal analyst and fellow at ESG, noted in DarkReading, “Interestingly, some progressive organizations believe that scalable, burstable cloud-based processing and storage resources can provide analytics opportunities they simply can’t achieve with homegrown on-premises efforts. This is particularly true with the application of machine-learning algorithms on massive security data sets.”
As environments grow, having the right engine to be able to support and scale with your business is critical to help future-proof your SOC.
InsightIDR leverages a combination of analytics, statistical anomaly detection, machine learning algorithms, and heuristic algorithms to identify both notable behaviors and alerts. The elasticity and scale needed to thoroughly monitor modern environments is only feasible in the cloud, which is a big part of why InsightIDR has been hosted in the cloud from its inception.
Stay ahead of attackers with intel from Rapid7’s Insight cloud and threat intelligence network
Much of the industry knows Rapid7 for our research and commitment to sharing intelligence freely with the broader security community. Research is not only a huge part of our culture, but it also informs a lot of the detections and capabilities we provide our customers. The InsightIDR detection library leverages insights from a number of intelligence sources, including:
- Metasploit, one of the most widely used penetration testing tools in the world.
- Project Heisenberg, Rapid7’s collection of honeypots that record telemetry to understand the tactics, techniques, and procedures used by attackers across the globe.
- Project Sonar, which actively analyzes public networks, providing internet-wide scanning to expose vulnerabilities.
These tools, along with a number of other research projects, insights from our data science team, and learnings from across our suite of security products in the Insight Cloud help us stay ahead or on top of the latest threats and ensure our customers do, too.
Security Planning Tip: As you’re evaluating detection technology, it’s important to understand the methodologies and sources that drive these detections. The threat landscape isn’t static; how will your team stay on top of the latest threats? It’s important to work this consideration into your plan as you look at tools and team structure.
Identify threats early with our comprehensive breadth of detections
The goal of detection technology is to find threats early and minimize the likelihood of attacker success in your environment. As modern environments grow, having multiple categories of detections helps ensure your environment is covered, and you have the coverage and context you need to remediate threats effectively.
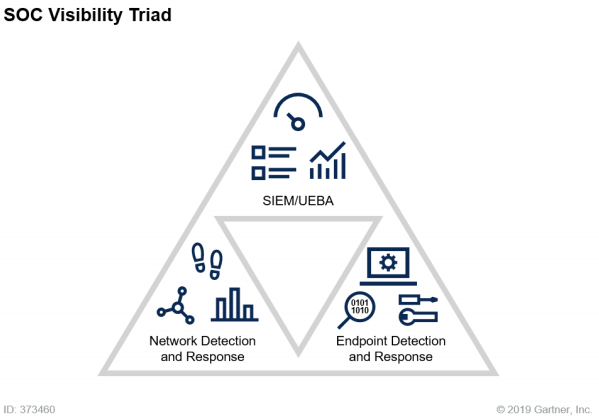
To accomplish this, InsightIDR has closely aligned our detection approach with Gartner’s SOC Visibility Triad. This triad focuses on three core pillars to achieve critical visibility and detections:
- Logs and user entity behavior analytics (UEBA)
- Network detection and response
- And endpoint detection and response
By combining these technologies in a single tool, teams are able to achieve a comprehensive, consolidated view of their most critical data and detections in one place.
Security Planning Tip: Gartner predicts that by 2025, three-quarters of large organizations will be pursuing security vendor consolidation strategies. That said, vendor consolidation alone can’t help drive efficiency or success. It’s important to keep revisiting your desired security and business outcomes throughout planning, and ensuring that any tools or processes you are looking to introduce can clearly help achieve those outcomes. With the right tool, a more consolidated approach can help decrease operational complexity and deliver greater SOC efficiency.
Avoid noise with reliable, expertly vetted detections
Finally, the last major point to consider when it comes to security planning and creating an updated detections strategy is alert volume. Too many security tools fire off endless alerts and make it impossible for teams to recognize actual threats when they happen. When it comes to alerts, it’s not about more—it’s about finding real threats fast.
The Rapid7 detections library is managed and curated by our own Managed Detection and Response team. Our MDR SOC specialists collaborate with our data scientists and intelligence teams to curate the most accurate and actionable alerts. This incremental layer of filtering helps eliminate noise that can distract from priority threat detection. In fact, our recent Total Economic Impact study reported a 27% reduction in false positives for customers compared to their previous SIEM.
As Jeffrey Gardner noted in the first installment of this series, for some teams it may make sense to augment your SOC with an MDR offering. With InsightIDR, even if you are exclusively leveraging just our software, you are still benefiting from the expertise and refinement of our MDR specialists built into our detections library out of the box.
Security Planning Tip: On paper, a list of alerts can look good, but understanding what it will actually mean in your environment and how your team will manage these is different. A trial or proof-of-concept experience can help offer some visibility into what alerting will actually look like in your environment and inform planning and resourcing efforts.
We hope these tips are helpful as you ramp up on planning! Please stay tuned for the rest of this series for more advice and ideas to make your security program a success going into the new year.
Start a free trial of InsightIDR today
Get Started
If you like the site, please consider joining the telegram channel or supporting us on Patreon using the button below.



![[HANDALA] - Ransomware Victim: Hotam EC 6 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)