Researchers warn of 100,000 industrial control systems exposed online

About 100,000 industrial control systems (ICS) were found on the public web, exposed to attackers probing them for vulnerabilities and at risk of unauthorized access. Among them are power grids, traffic light systems, security and water systems.
Exposed ICSs include units (sensors, actuators, switches, building management systems, and automatic tank gauges) for critical infrastructure systems.
Cybersecurity company BitSight alerted of the threat after identifying the problem in multiple sectors and impacting many Fortune 1000 companies in 96 countries.
Bitsight told BleepingComputer its analysts could draw data from mass-scale scans of the entire IP address space and the logs produced from this, allowing them to identify multiple protocols and to determine the type of system at each address.
Bitsight says it processes approximately 400 billion security events daily and actively monitors over 40 million organizations worldwide, with its vast collection of datasets going back several years.
Scale of the problem
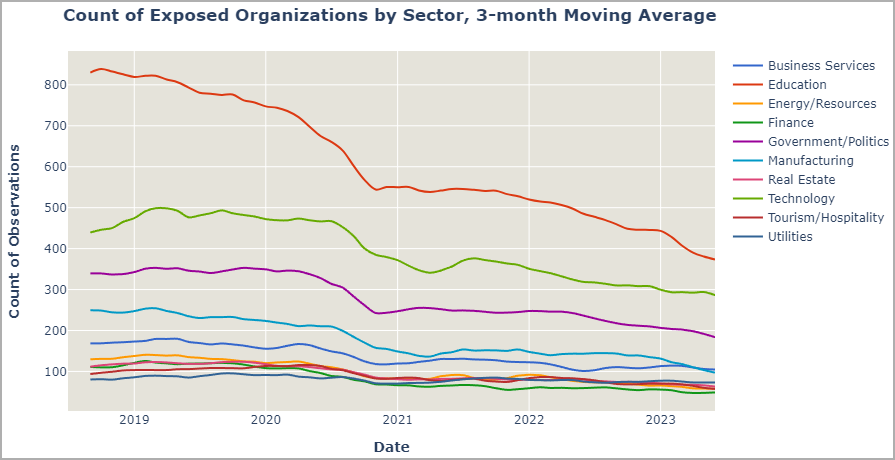
BitSight reports that its data shows that things got better year over year, with the number of exposed devices dropping since 2019.
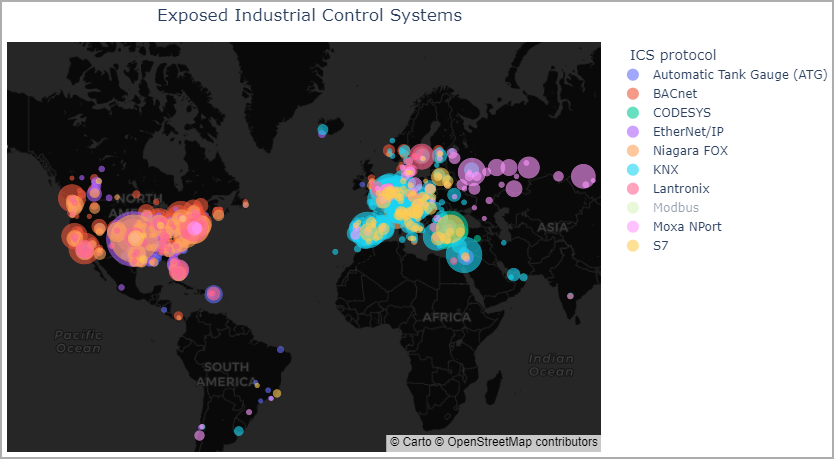
The most exposed countries in terms of how many organizations have at least one exposed ICSs in them are:
- United States
- Canada
- Italy
- United Kingdom
- France
- Netherlands
- Germany
- Spain
- Poland
- Sweden
In terms of which sectors are the least secure when it comes to ICS security, Bitsight says that Education, Technology, Government, Business Services, Manufacturing, Utilities, Real Estate, Energy, Hospitality, and Finance stand out.
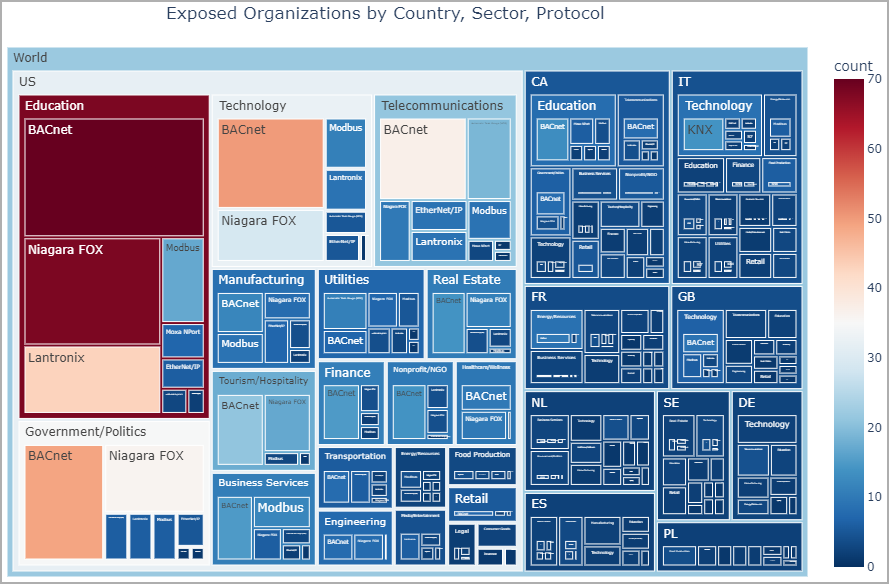
BitSight has also created the following diagram to correlate countries, sectors, and exposed protocols.
Risk evaluation
Industrial systems are not exempt from critical vulnerabilities, which can impact a wide range of ICS as well as more specific but widely used tools.
Previously, Kaspersky estimated that roughly 20% of all deployed ICSs are vulnerable to critical-severity flaws.
The cases of malware infections by state-sponsored hackers or cyberattacks by opportunistic threat actors targeting ICSs abound, and the authorities in the U.S. have issued relevant warnings multiple times, urging system administrators to secure the critical infrastructure under their control.
However, based on Bitsight’s data alone, it is difficult to estimate how many of the 100,000 exposed ICSs are exploitable and the level of damage hackers can deal with an attack.
For secure remote access to Industrial Control Systems (ICS), organizations should implement at least basic security measures like VPN access, multi-factor authentication (MFA), role-based access control (RBAC), and network segmentation.
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[LYNX] - Ransomware Victim: Greta Group 6 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
