The Week in Ransomware – November 17th 2023 – Citrix in the Crosshairs

Ransomware gangs target exposed Citrix Netscaler devices using a publicly available exploit to breach large organizations, steal data, and encrypt files.
The threat actors exploit the Citrix Bleed vulnerability (CVE-2023-4966), which was disclosed last month and continues to be abused in attacks.
Security researcher Kevin Beaumont, who has been tracking the attacks, has found that many recent victims also utilized vulnerable Citrix Netscaler devices at the time of the attack, allowing initial access to the corporate network.
Some companies that recently suffered a cyberattack and utilized vulnerable Citrix Netscaler devices include Toyota Financial Services, Industrial and Commercial Bank of China (ICBC), DP World, Allen & Overy, and Boeing.
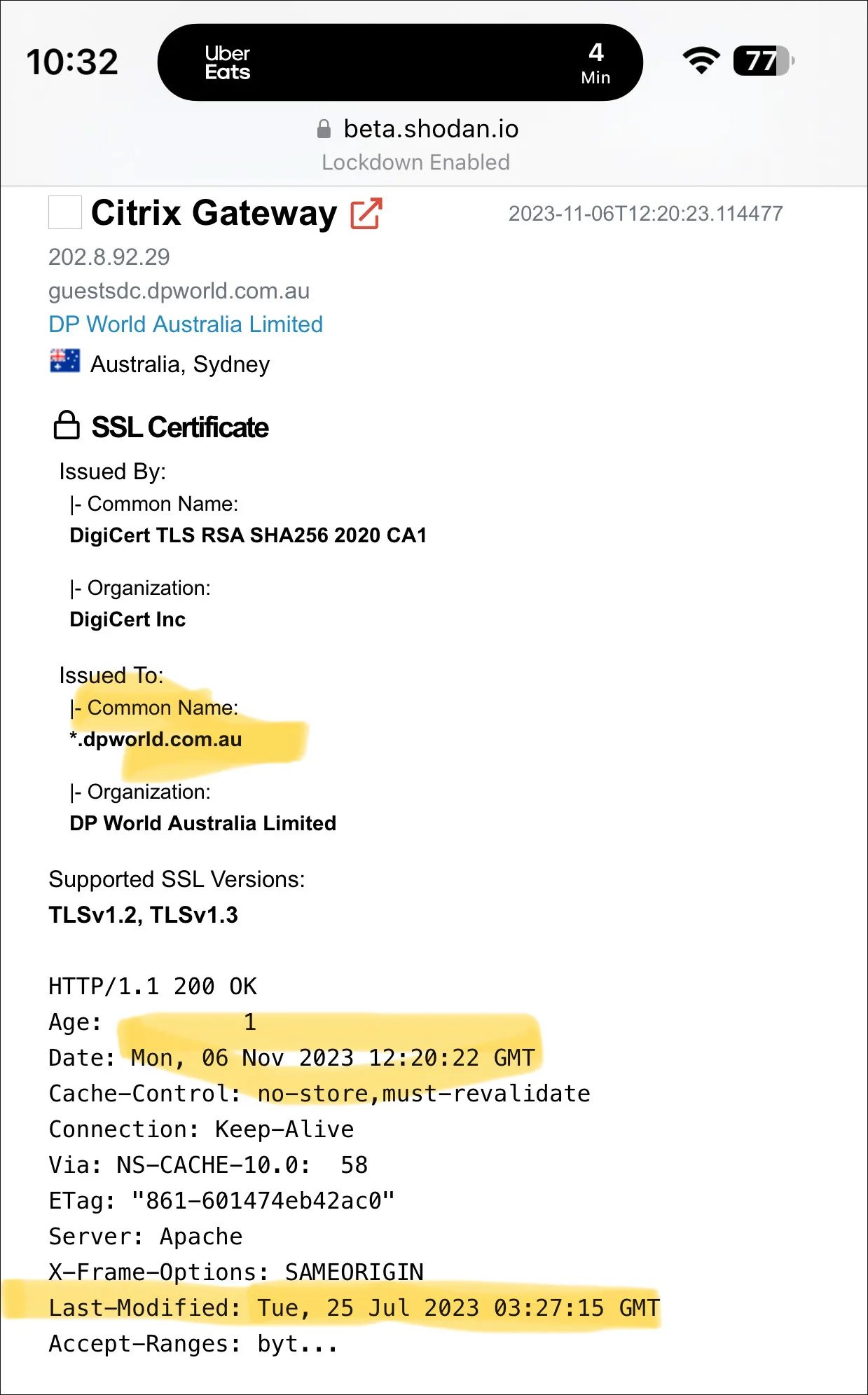
Source: Kevin Beaumont
While it is known that affiliates for the LockBit and Medusa ransomware gangs are behind some of these attacks, it is likely widely being exploited by other criminal operations.
In other news, the BlackCat ransomware gang took the bold step of filing an SEC complaint on one of its victims for not disclosing they suffered a cyberattack.
The threat actors tried to get the company into trouble for a new SEC rule that requires publicly traded companies to report cyberattacks within four days if they have a material impact. However, this rule does not go into effect until December 15th, 2023.
While many ransomware gangs have threatened to report cyberattacks to the SEC if a ransom was not paid, this could be the first publicly disclosed use of the extortion strategy.
We also learned more about recent attacks and tactics used by ransomware threat actors, which are highlighted below:
- The FBI shared tactics of Scattered Spider, an English-speaking affiliate of BlackCat ransomware.
- The FBI says Royal ransomware demanded 350 victims to pay $275 million in ransoms.
- FBI and CISA released an advisory on the Rhysida ransomware operation.
- The Toronto Public Library confirmed data was stolen in a recent Black Basta ransomware attack.
- A Yamaha subsidiary and the British Library confirmed that ransomware caused recent attacks.
Contributors and those who provided new ransomware information and stories this week include: @serghei, @demonslay335, @billtoulas, @fwosar, @Seifreed, @malwrhunterteam, @BleepinComputer, @Ionut_Ilascu, @LawrenceAbrams, @GossiTheDog, @BrettCallow, @PogoWasRight, @pcrisk, and @NCCGroupInfosec.
November 13th 2023
FBI: Royal ransomware asked 350 victims to pay $275 million
The FBI and CISA revealed in a joint advisory that the Royal ransomware gang has breached the networks of at least 350 organizations worldwide since September 2022.
Don’t throw a hissy fit; defend against Medusa
Not to be confused with MedusaLocker, Medusa was first observed in 2021, is a Ransomware-as-a-Service (RaaS) often using the double extortion method for monetary gain. In 2023 the groups’ activity increased with the launch of the ‘Medusa Blog’. This platform serves as a tool for leaking data belonging to victims.
Key Ransomware Indicator Up 56% Year-on-Year: October Data
In October attacks fell by 15.12% from the prior month according to the volume of victims posted on ransomware leak sites, but remained high from a year-on-year perspective with a 54.67% increase over October 2022. Last month also marked the tenth consecutive with a YoY increase in ransomware victims posted to leak sites, and the eighth consecutive with a count above 300.
New 1337 Ransomware
PCrisk found a new 1337 Ransomware that appends the .1337 extension and drops a ransom note named yourhope.txt.
November 14th 2023
LockBit ransomware exploits Citrix Bleed in attacks, 10K servers exposed
The Lockbit ransomware attacks use publicly available exploits for the Citrix Bleed vulnerability (CVE-2023-4966) to breach the systems of large organizations, steal data, and encrypt files.
New GlobeImposter variant
PCrisk found a new GlobeImposter variant that appends the .Pig865qq extension.
November 15th 2023
Ransomware gang files SEC complaint over victim’s undisclosed breach
The ALPHV/BlackCat ransomware operation has taken extortion to a new level by filing a U.S. Securities and Exchange Commission complaint against one of their alleged victims for not complying with the four-day rule to disclose a cyberattack.
Toronto Public Library confirms data stolen in ransomware attack
The Toronto Public Library (TPL) confirmed that the personal information of employees, customers, volunteers, and donors was stolen from a compromised file server during an October ransomware attack.
FBI and CISA warn of opportunistic Rhysida ransomware attacks
The FBI and CISA warned today of Rhysida ransomware gang’s opportunistic attacks targeting organizations across multiple industry sectors.
New ransomware variant
PCrisk found a new ransomware variant that appends the .shanova extension and drops a ransom note named read_it.txt.
November 16th 2023
FBI shares tactics of notorious Scattered Spider hacker collective
The Federal Bureau of Investigation and the Cybersecurity and Infrastructure Security Agency released an advisory about the evasive threat actor tracked as Scattered Spider, a loosely knit hacking collective that now collaborates with the ALPHV/BlackCat Russian ransomware operation.
Toyota confirms breach after Medusa ransomware threatens to leak data
Toyota Financial Services (TFS) has confirmed that it detected unauthorized access on some of its systems in Europe and Africa after Medusa ransomware claimed an attack on the company.
New STOP ransomware variants
PCrisk found new STOP ransomware variants that append the .eqza and .eqew extensions.
November 17th 2023
British Library: Ongoing outage caused by ransomware attack
The British Library confirmed that a ransomware attack is behind a major outage that is still affecting services across several locations.
Yamaha Motor confirms ransomware attack on Philippines subsidiary
Yamaha Motor’s Philippines motorcycle manufacturing subsidiary was hit by a ransomware attack last month, resulting in the theft and leak of some employees’ personal information.
That’s it for this week! Hope everyone has a nice weekend!
A considerable amount of time and effort goes into maintaining this website, creating backend automation and creating new features and content for you to make actionable intelligence decisions. Everyone that supports the site helps enable new functionality.
If you like the site, please support us on “Patreon” or “Buy Me A Coffee” using the buttons below
To keep up to date follow us on the below channels.

![[FLOCKER] - Ransomware Victim: G*********************y[.]org 3 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

