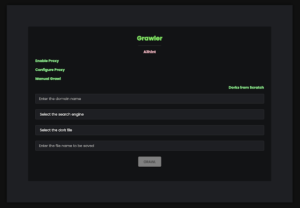
Grawler – Tool Which Comes With A Web Interface That Automates The Task Of Using Google Dorks, Scrapes The Results, And Stores Them In A File
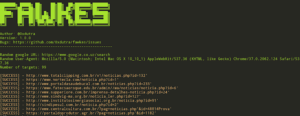
Grawler is a tool written in PHP which comes with a web interface that automates the task of using google...















![[J] - Ransomware Victim: ****[.]com[.]au 25 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)
