Malware Analysis – smokeloader – 2df7d13ddf98555c1c140b60fee0cb11
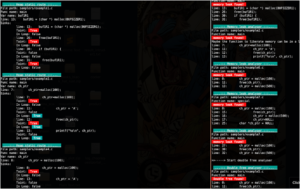
Score: 10 MALWARE FAMILY: smokeloaderTAGS:family:smokeloader, backdoor, trojanMD5: 2df7d13ddf98555c1c140b60fee0cb11SHA1: aaf82760a8461b48452b69fa7c44e2dd1630518fANALYSIS DATE: 2023-02-07T16:31:04ZTTPS: T1012, T1120, T1082 ScoreMeaningExample10Known badA malware family was detected.8-9Likely...



![[TRYHACKME] - Void Execution Challenge 5 void_execution](https://www.redpacketsecurity.com/wp-content/uploads/2025/09/void_execution.png)


![[TRYHACKME] - Void Execution Challenge 8 void_execution](https://www.redpacketsecurity.com/wp-content/uploads/2025/09/void_execution-150x150.png)










![LockBit 3.0 Ransomware Victim: cantinatollo[.]it 24 image-11](https://www.redpacketsecurity.com/wp-content/uploads/2022/06/image-11-300x142.png)
![Cobalt Stike Beacon Detected - 23[.]95[.]67[.]59:8443 25 Cobalt-Strike](https://www.redpacketsecurity.com/wp-content/uploads/2021/11/Cobalt-Strike-300x201.jpg)

![[HANDALA] - Ransomware Victim: Saturday Unveilings – Shadows Have Names 42 image](https://www.redpacketsecurity.com/wp-content/uploads/2024/09/image-300x300.png)

